What is Multifactor Authentication and How Does it Work?

Multifactor Authentication (MFA) is a verification mechanism to ensure that only authorised users can access an account, a VPN, or an application. MFA requires users to provide at least two types of information before accessing organisational data to prove their identity.
By default, enterprise accounts require only a single authentication factor, such as a PIN or a password, to verify users. This can increase the attack surface as passwords are vulnerable to brute forcing. MFA requires users to submit more than a simple password for optimum security.
Why is Multifactor Authentication Important?
- Prevents Identity & Credential Thefts
Multifactor Authentication (MFA) safeguards any system by reducing the chances of identity and credentials thefts.
- Protects Against the Vulnerabilities of Weak Passwords
MFA demands more than two authentications to access critical resources. So even when a user sets up a weak password, the mechanism adds another layer of protection to prevent password guessing attacks.
- Enhances User Experience
MFA ensures many authentication options to choose from. Apart from passwords, MFA offers the flexibility for users to verify themselves with their fingerprints, facial scans, and voice recognitions.
- Strengthens Security Architecture
The authentication mechanism improves an organisation’s security posture by providing integrated security and an extra layer of protection for your enterprise infrastructure.
How Does Multifactor Authentication work?
When a user attempts to access enterprise technology or resources, MFA requires various forms of information from a user. The goal of the mechanism is to provide access to only authorised users. To achieve this, MFA leverages different types of high-level authentication factors rather than relying on just usernames and passwords.
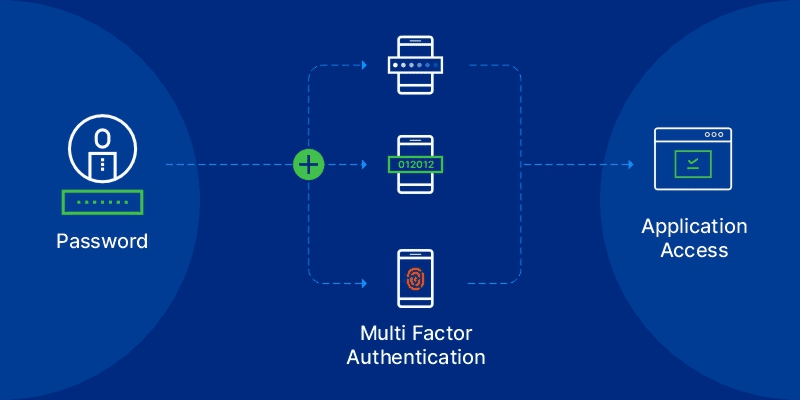
What are the Three Types of Authentication Factors Used by MFA?
- Knowledge
As the name indicates, the knowledge factor consists of the details that are based on a user’s memory. Passwords, PINs, passphrases, and the correct answers to security questions are all examples of such factors. But users’ basic personal information is prone to sophisticated phishing and social engineering attacks. Hence solely relying on a set of knowledge-based security questions for providing user access is not suggested for authentication.
- Possession
Knowledge-based factors are vulnerable to cyber attacks. So, in the second stage of authentication, MFA asks users to provide something they have in their possession. Examples include key fobs, cell phones, and credit cards, which are more secure since they store or receive login credentials. For instance, SMS authentication sends an MFA code or a One-Time Password (OTP) to a user’s mobile device. However, devices only provide a medium level of security since they may be lost or stolen. Or, in the worst case, get infected by malware.
- Inherence
The inherence factor is the most secure mode of authentication available. Users authenticate themselves with what they are, such as their fingerprints, facial scans, retinal scans, or voice recognition. This is the third stage of MFA, and it protects systems from unauthorised access and misuse, even if an attacker has already fooled other safeguards.
What is the Difference between Two-Factor Authentication and Multifactor Authentication?
Two-Factor authentication is another term that is often used in place of MFA. Two-Factor Authentication (2FA) only uses two forms of authentication. MFA lets one use as many authentication factors as one wants. Typically, 2FA falls under Multifactor Authentication. Any implementation of MFA is also a 2FA implementation. However, 2FA is not always used in all MFA instances.
Single-Factor Authentication is less safe than Multifactor or Two-Factor Authentication. Thus, MFA is preferred over 2FA because it adds another layer of protection against hackers. However, the robustness of an MFA system depends on the reliability of its supplementary authentication mechanisms.
Conclusion
The digital world is rapidly moving towards the adoption of technologies such as the cloud to store critical data. On the other hand, the number of user identities is also increasing, expanding the risks of user credential thefts. Hence, having a foolproof Multifactor Authentication mechanism in place can prevent enterprise user account abuse.
Here is a solution brief for you to get an in-depth insight into how Multifactor Authentication can solve some pressing problems for enterprises. In this solution brief, we also talk in detail about the capabilities of modern-day MFA solutions.
Planning to neutralize the risks of illegitimate access? Sectona Security Platform’s built-in adaptive MFA gives you a robust plug and play experience. Book a demo today to explore more.



