Privileged Access Governance
Govern privileged entitlements, access to privileged access platform, account inventory to secure & comply.
Move away from manual script based reviews with automated privileged access review system.
Why Review & Certify Access & Entitlement?
Technology infrastructure & operations environments are complex. External vendor relationships add more complexity. Most of the users hold more access than they require at any given time.Remove Excessive Privileges
Schedule & set multiple reviews simultaneously based on account type, asset type or high risk accounts.
Reduce Risk of Perpetual Granted Excessive privileges
Delegate review rights & periodically review access to manage risk of permanent access to accounts.
Privileged Access Reviews Made Easy

Prove Compliance Controls with Simplified Privileged Access Certification
Prove compliance controls with delegated responsibility to approves and owners. Define data filters, approval levels and action manager and bring multiple members on a common platform.
Periodically Review Access to PAM Platform
Schedule period reviews and be prepared to manage audits with confidence.
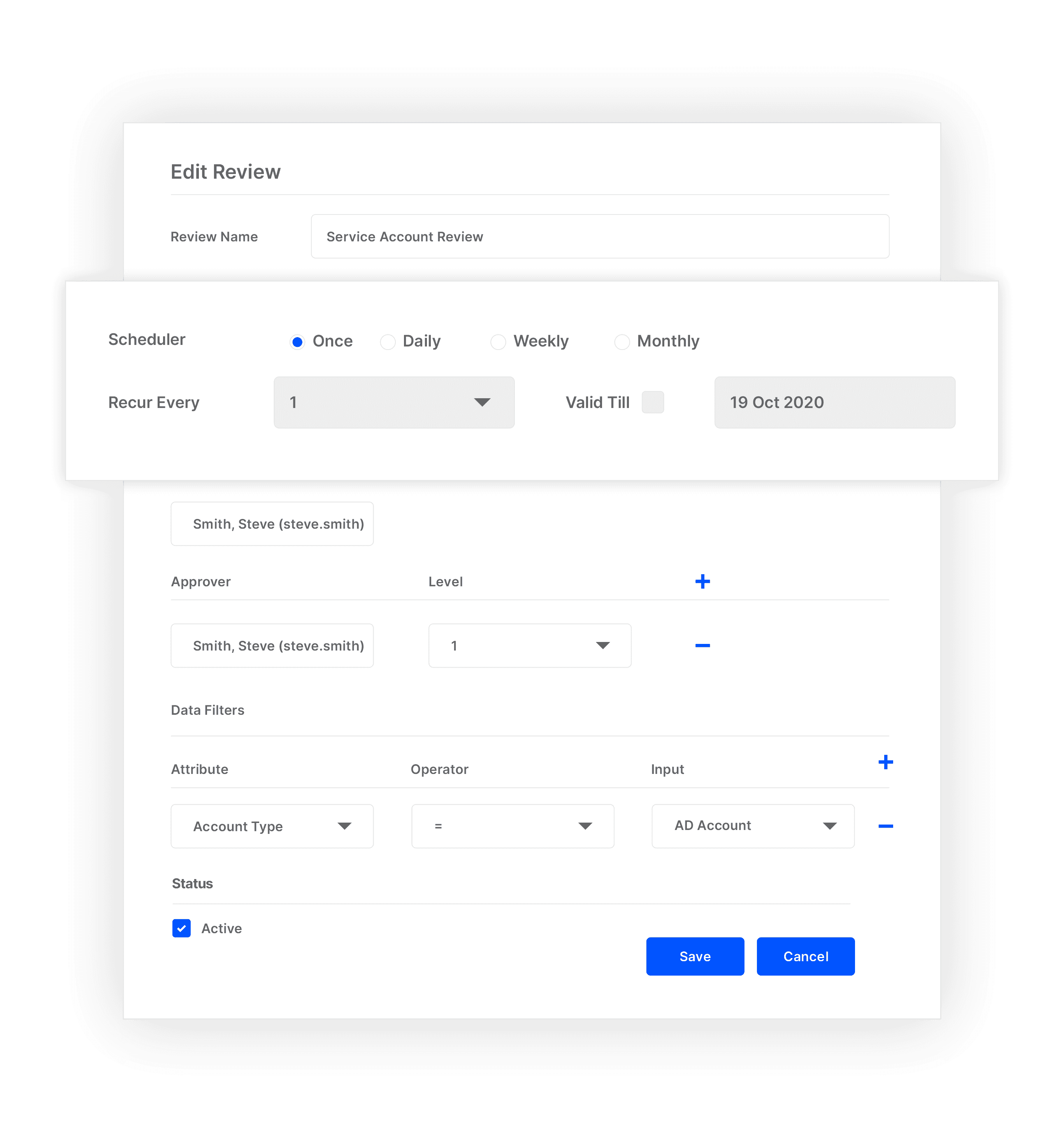
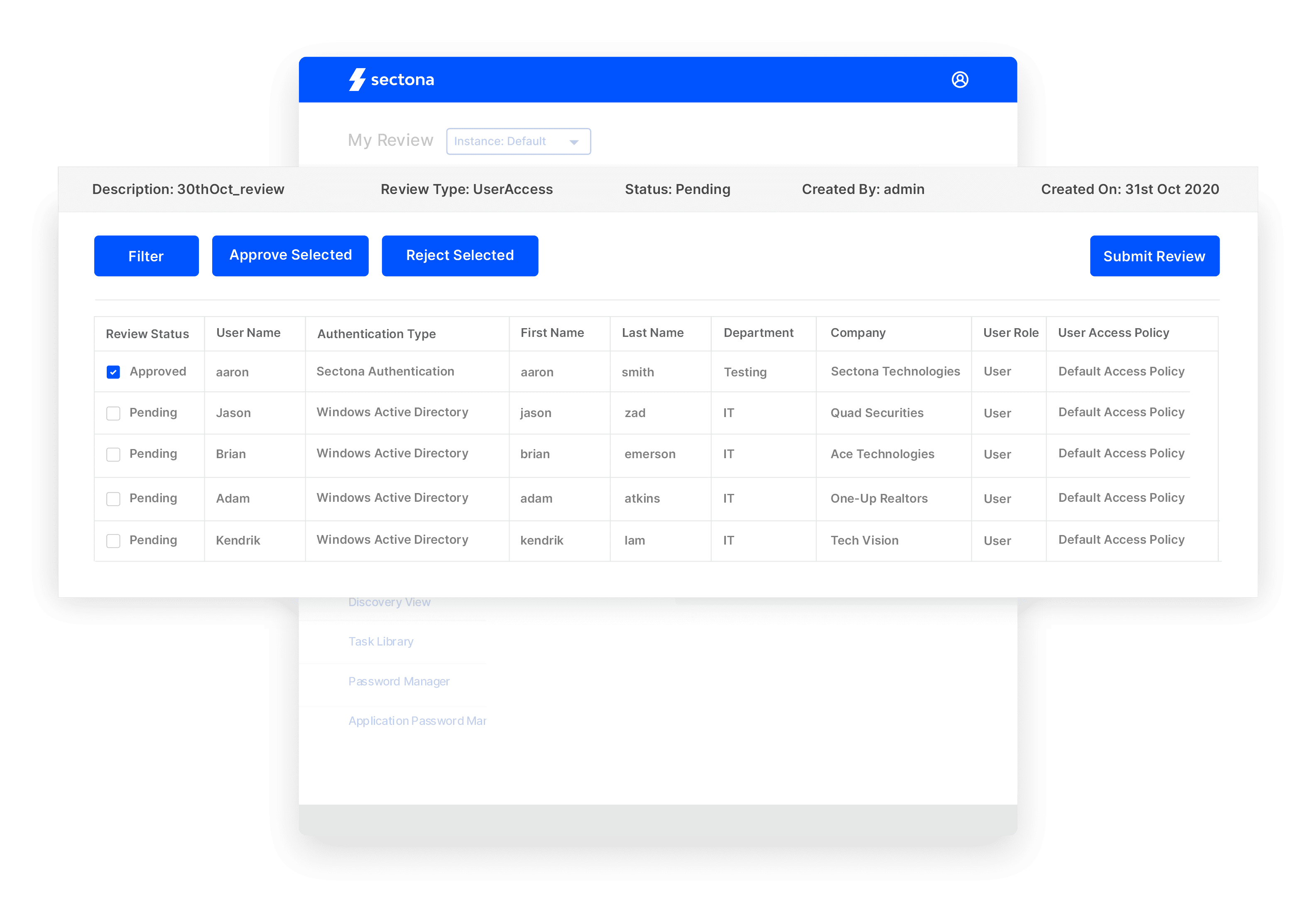
Certify & Review Privileged Entitlements
Managers can easily respond to access review and certification requests in a centralized system.



Start Discovering your Assets and Privileged Accounts
How Privileged Access Governance works

Explore the Platform
Achieve more with easy to configure integrated components.
Password Management
Manage and rotate passwords & ssh keys with embedded & encrypted vaulting.
Session Recordings & Threat Analytics
Advanced session monitoring for all privileged activities with risk-profiling & behaviour-based analytics.
Just-in-Time Access
Remove standing privileges and leverage combination of approaches to implement JIT policy.
Privileged Task Management
Reduce risk of excessive privilege by automating & delegating IT operations task.
Account Lifecycle Management
Streamline account provisioning, deprovisioning & operations with complete control.



