Just in time access
Remove standing privileges and leverage combination of approaches to implement just in time policies.
Poor IAM practices, stolen credentials and privilege account abuse attribute to most prominent cyber attacks.
Limit Exposure
Lock down access to critical privileged accounts by dynamically enabling/disabling or elevating privileged access with built-in provisioning/deprovisioning.
Automate Routine Tasks
Control actions of privileged users by placing limitations on what a user is allowed to do.
No Specifc Device Level Knowledge Required
Operators do no need specific device level knowledge to run and execute jobs.
Combine Vaulting and Session Management
with JIT Approach
Selectively Implement JIT Policies
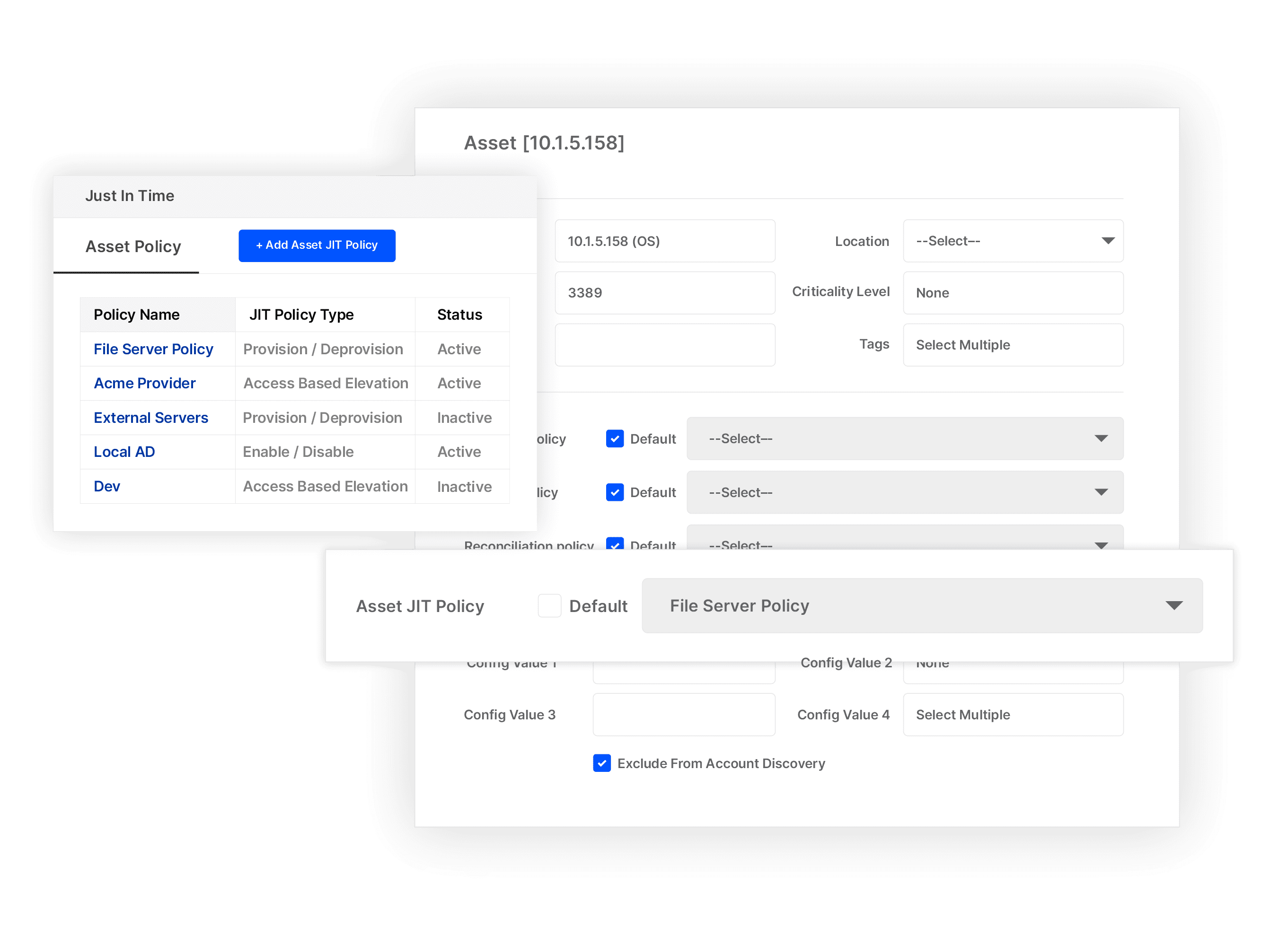
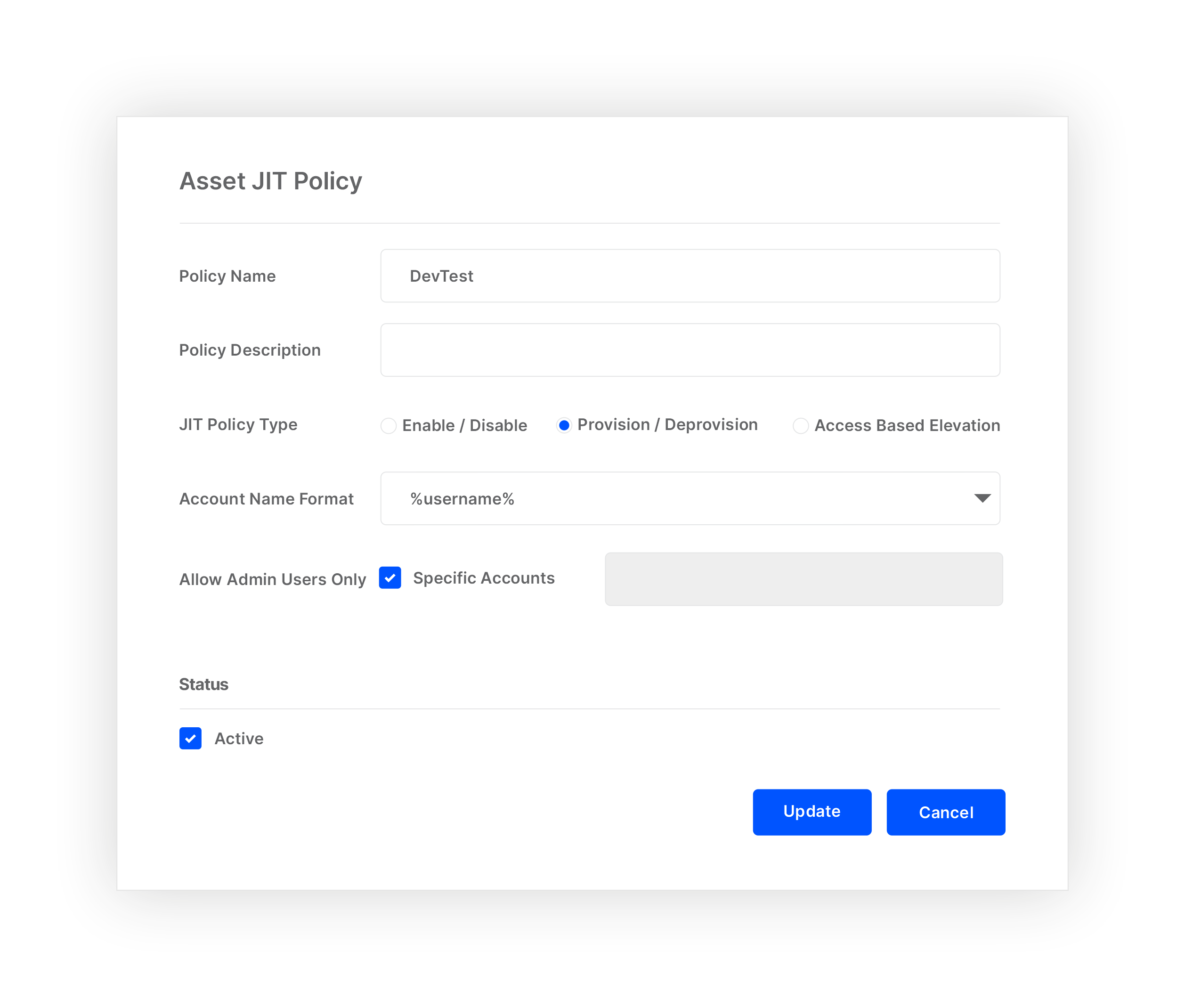
Define custom JIT access methods (Enable/Disable, Provisioning/De-provisioning, Elevation) for securing assets based on user access type.
Secure Access to AWS Management Console with Ephemeral Token
Secure access to root / IAM Administrator using AWS Token based integration combined with session recording.
Use Ephemeral Accounts to Provide Vendor Access
Leverage provisioning / de-provisioning capabilities to allow vendors to get access to assets anywhere based on a workflow request.



Start Discovering your Assets and Privileged Accounts
How Just-In-Time Access Works


Explore the Platform
Achieve more with easy to configure integrated components.
Password Management
Manage and rotate passwords & ssh keys with embedded & encrypted vaulting.
Session Recordings & Threat Analytics
Advanced session monitoring for all privileged activities with risk-profiling & behaviour-based analytics.
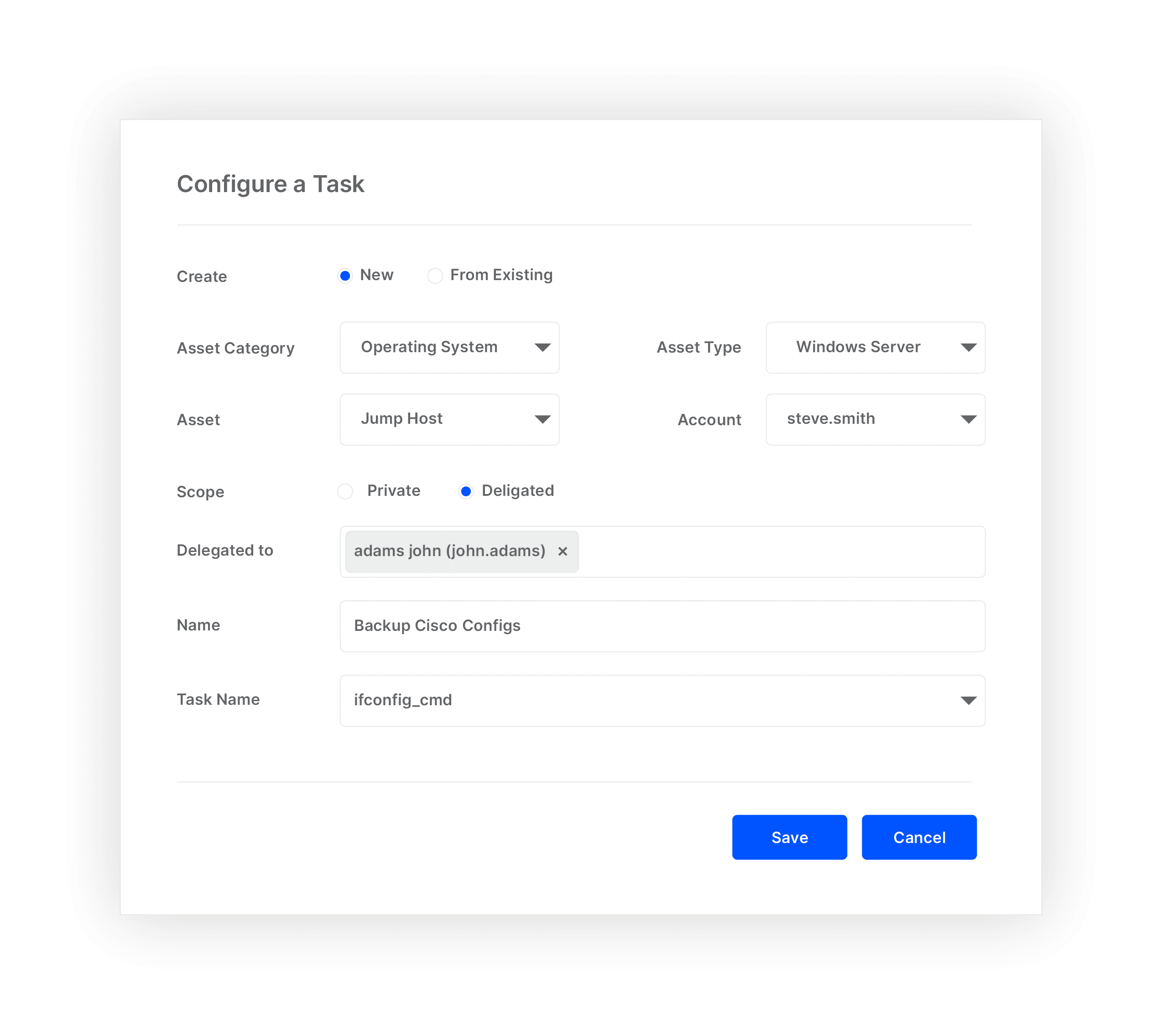
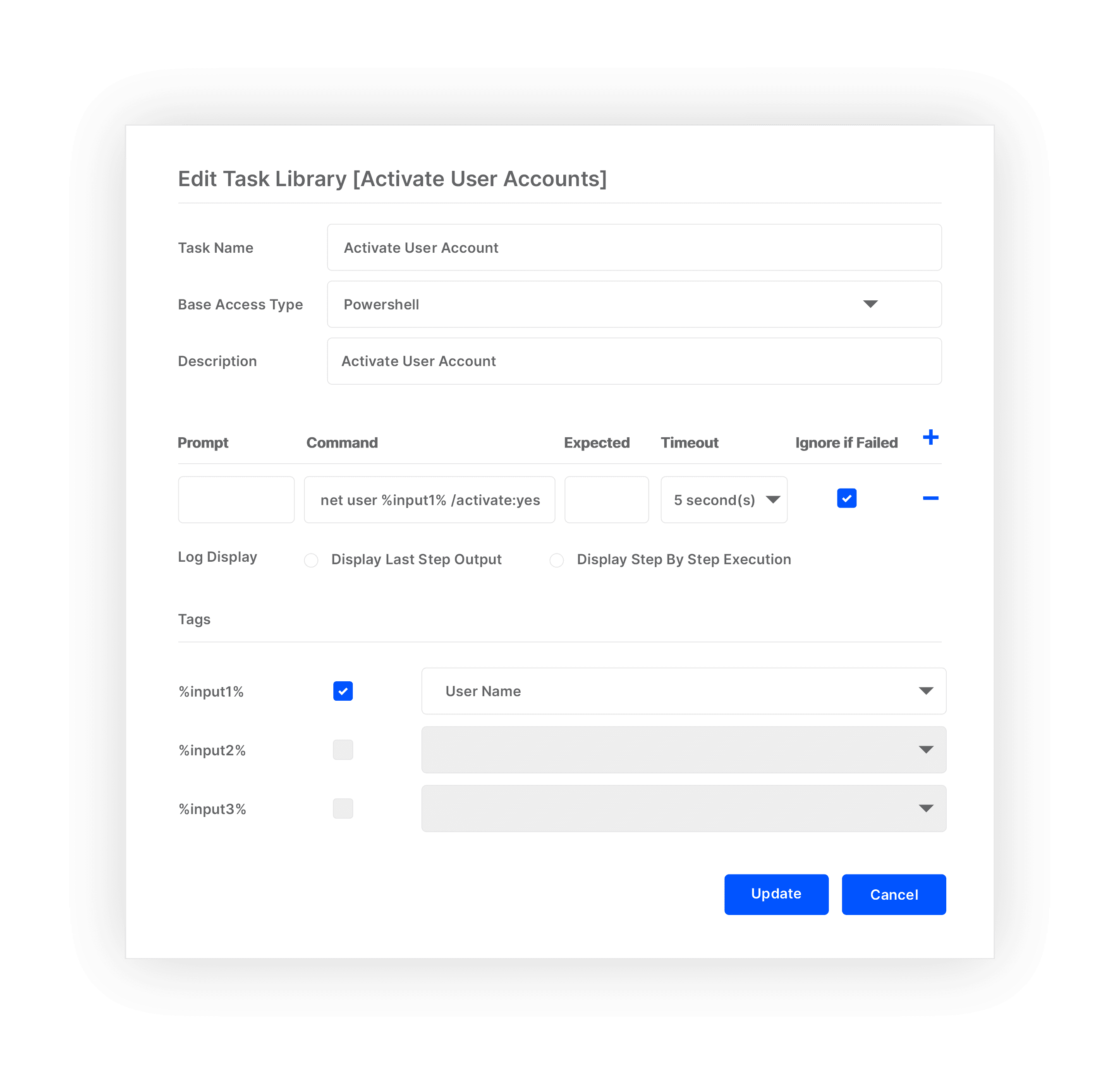
Privileged Task Management
Reduce risk of excessive privilege by automating & delegating IT operations task.
Account Lifecycle Management
Streamline account provisioning, deprovisioning & operations with complete control.
Windows Privilege Management
Control & secure administrator account usage on your organization’s Windows systems.





