Continuous Discovery
Modern infrastructure is dynamic. Secure privileged accounts with continuous discovery and vaulting.
Achieve upto 99% reduction in time for reconciling privileged accounts.
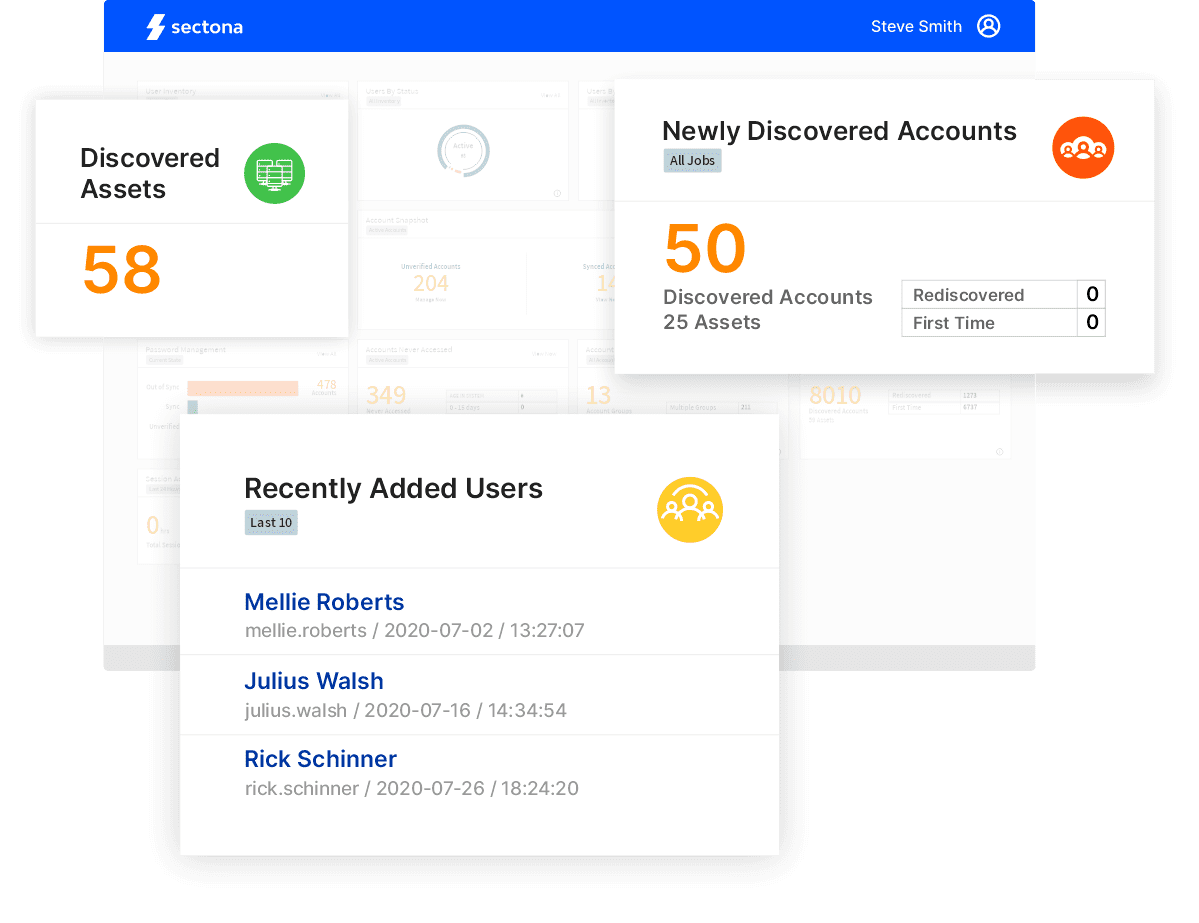
Continuous Discovery at Scale
Stay in control of newly added IT assets and unknown or hidden privileged accounts spread across your IT.
Reduce Time for Integration
With schedulers and automated onboarding rules, obtain relevant asset information and reduce time in securing privileged accounts.
Deeper Discovery Capabilities
Manage dependent services and SSH keys to secure risky application credentials.
Discover Assets and Accounts at Automation Scale
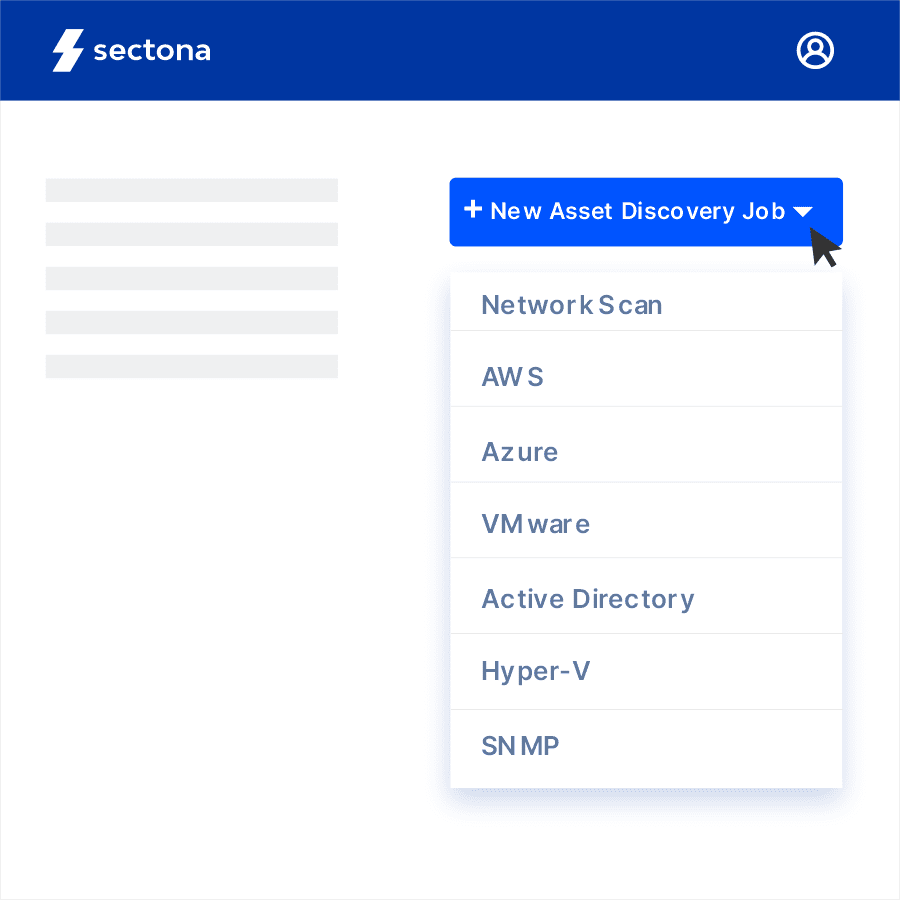
Effortlessly Discover Assets
Leverage comprehensive yet flexible asset discovery techniques using network scans, AWS resource discovery, Azure discovery, VM ware and Hyper-V resource scan and Active Directory.
Discover Local and Service Accounts
Do more with discovered accounts by classifying and vaulting local, unknown and hidden privileged accounts. Manage dependent services and SSH keys to secure risky application credentials.



Start Discovering your Assets and Privileged Accounts
How Continuous Discovery Works
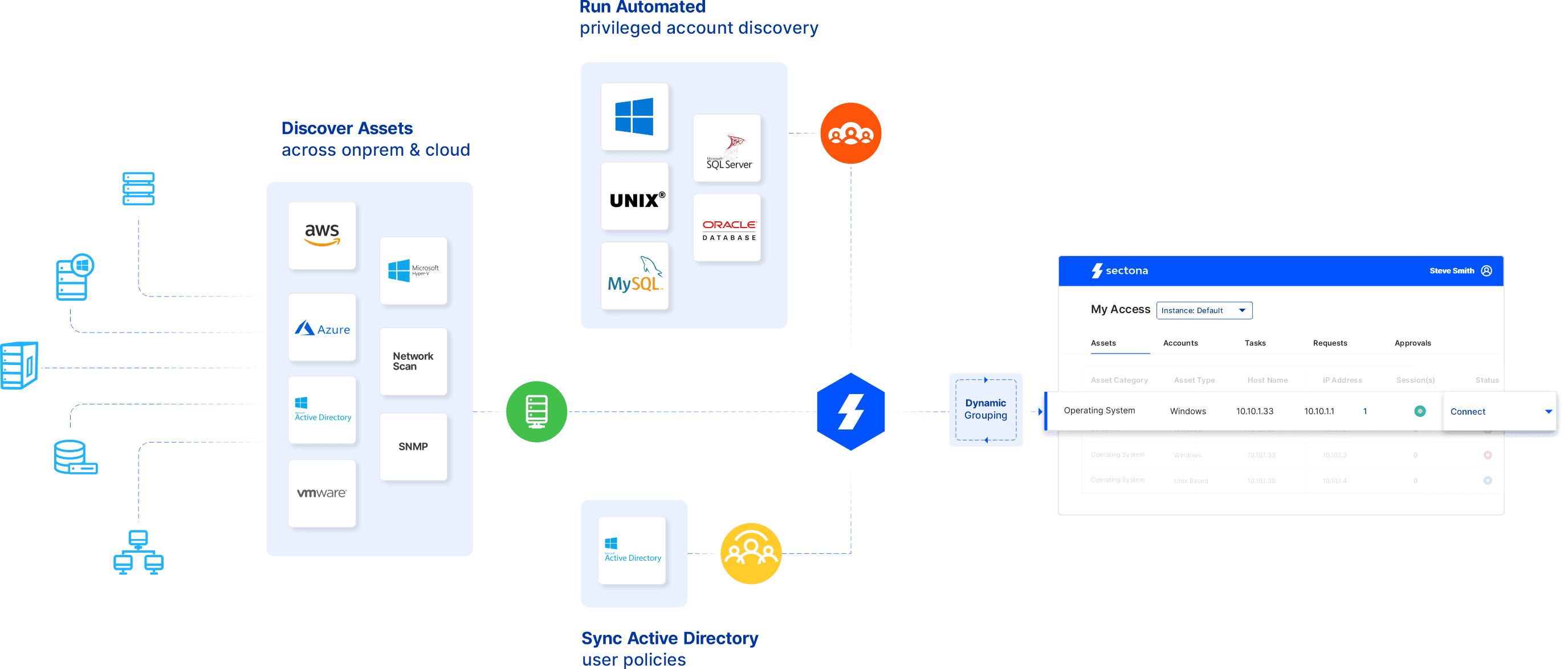
Integrations
Why Enterprises Trust Us

Staying relevant in modern times by securing access to AWS infrastructure.
Read Case StudyExplore the Platform
Achieve more with easy to configure integrated components
Password Management
Manage and rotate passwords and SSH keys with embedded and encrypted vaulting.
Session Recordings and Threat Analytics
Advanced session monitoring for all privileged activities with risk-profiling and behavior-based analytics.
Just-in-Time Access
Remove standing privileges and leverage a combination of approaches to implement JIT policy.
Privileged Task Management
Reduce risk of excessive privilege by automating and delegating IT operations task.
Account Lifecycle Management
Streamline account provisioning, de-provisioning, and operations with complete control.
Windows Privilege Management
Control and secure administrator account used on your organization’s Windows systems.
Privileged Access Governance
Govern privileged entitlements, access to privileged access platform, account inventory to secure & comply
DevOps Secrets Management
Consolidate secrets across applications, tools & non-human interaction under a secure audit-able infrastructure



