Core administrators
Remote vendors
Developer users
Manage privileges confidently!
Accelerate Privilege Management Transformation
Secure passwords, SSH keys and secrets with Sectona’s purpose-built vault.
Govern privileges and isolate endpoints leveraging best-in-class cross-platform session management technology.
Govern privileges and isolate endpoints leveraging best-in-class cross-platform session management technology.
Realize More Value
Integrated privileged management for diverse IT Teams
Do More With Less
Designed to help you secure endpoints, workloads and applications with a consolidated dashboard
Achieve More
Purpose built to cater to emerging security needs capable of handling scalability and complex enterprise requirements
USE CASES
From securing what matters to mitigating advanced access challenges
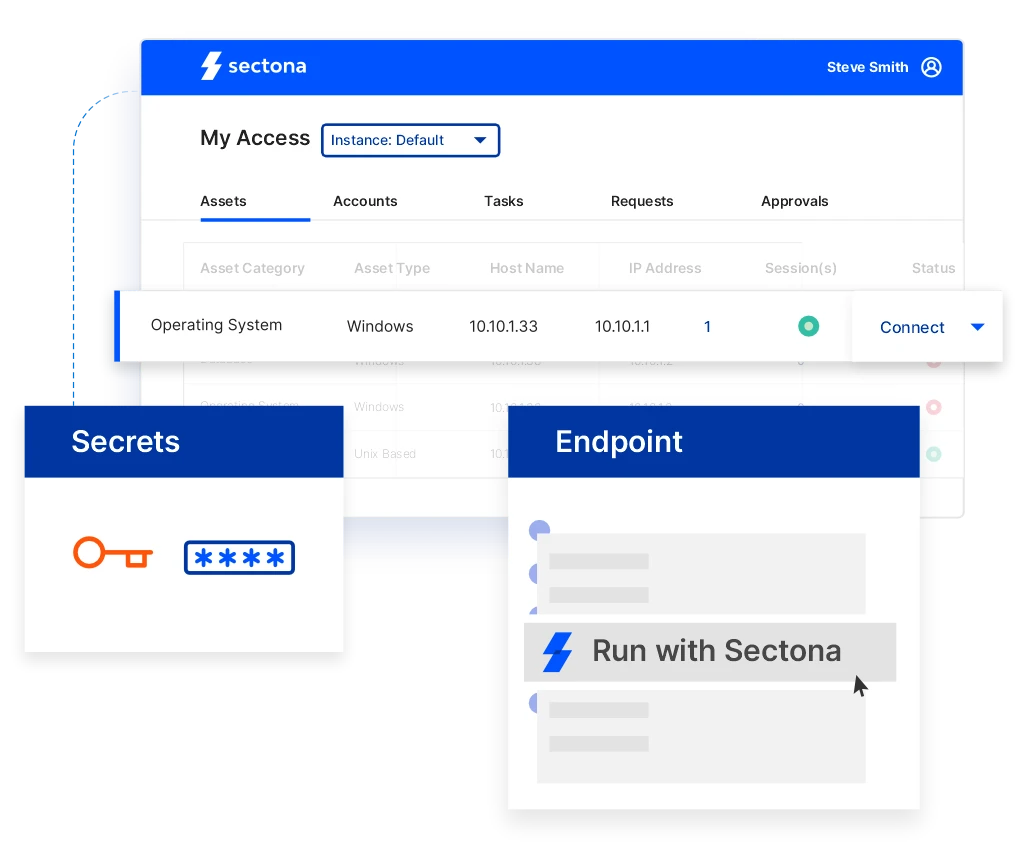
Centrally store, manage and rotate secrets and passwords
Manage, secure, and rotate passwords, SSH keys, and secrets within the solution’s purpose-built vault
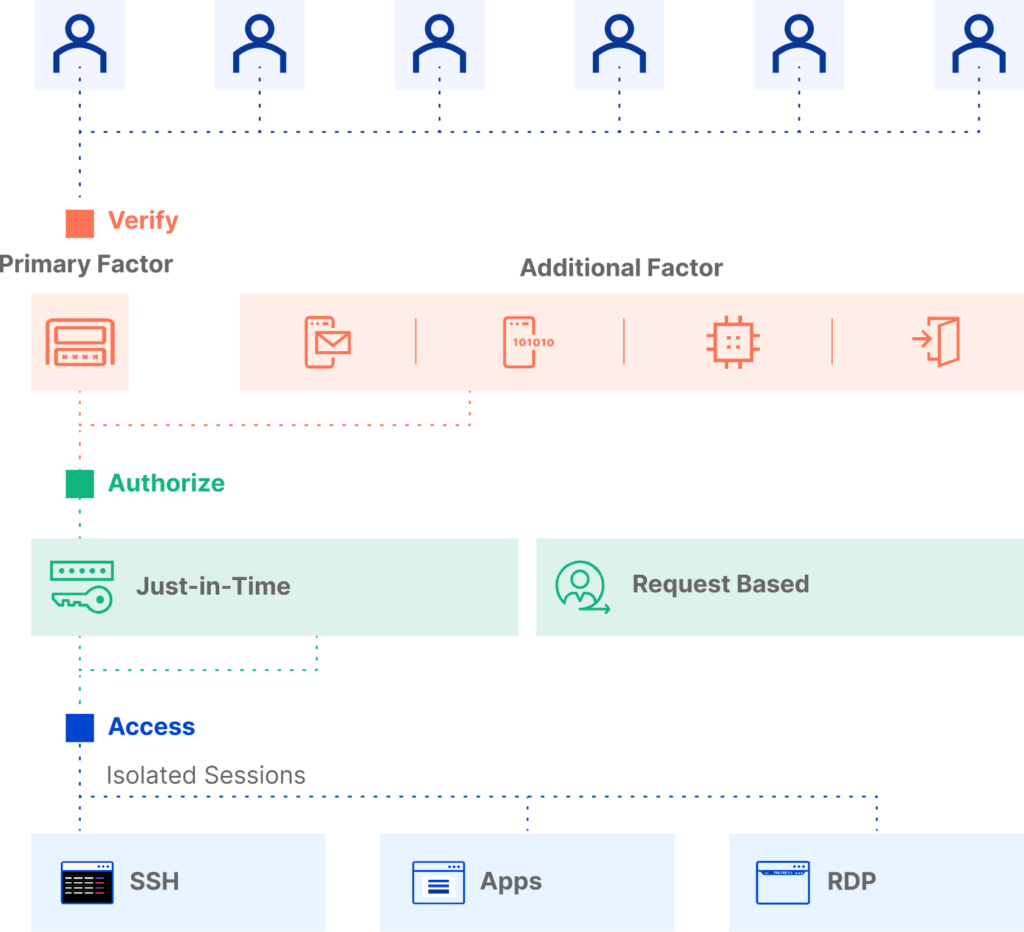
Secure privileged access for any user from any device
Leverage cross-platform session management technology to manage and govern privileged user access from anywhere
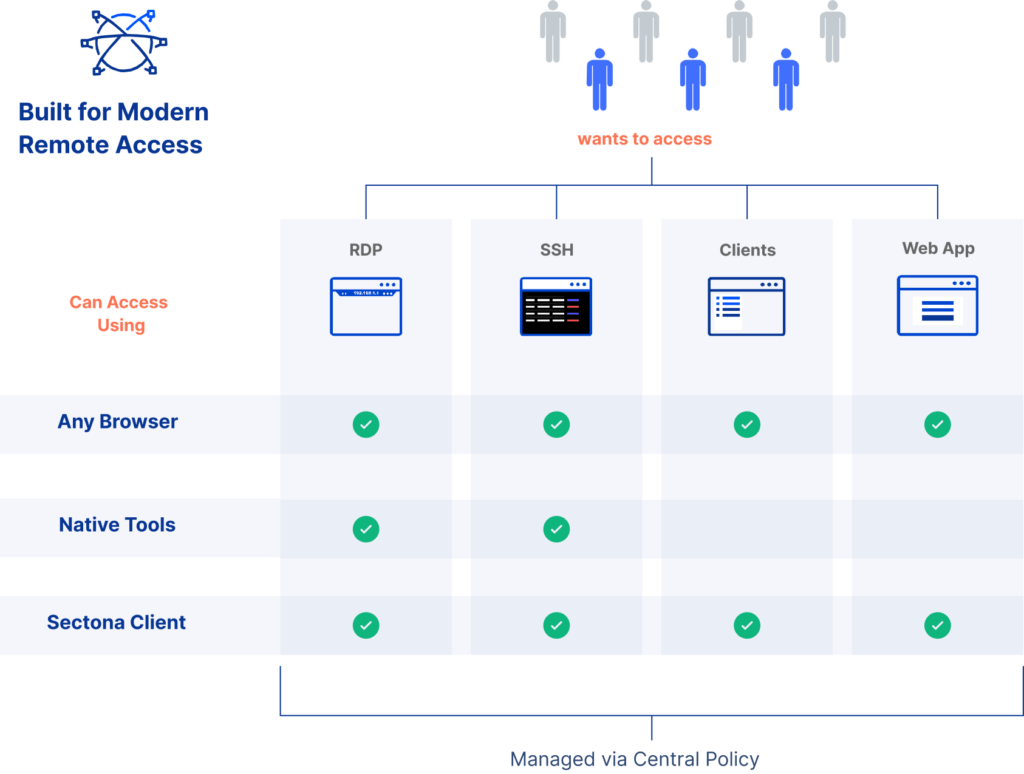
Empower access to IT teams with hybrid access mechanisms
Define and streamline secure user access via browser, client, native utilities, or jump server, based on critical parameters
Continuous access automation
Simplify PAM operations and lifecycle with comprehensive discovery and onboarding at both asset and account level
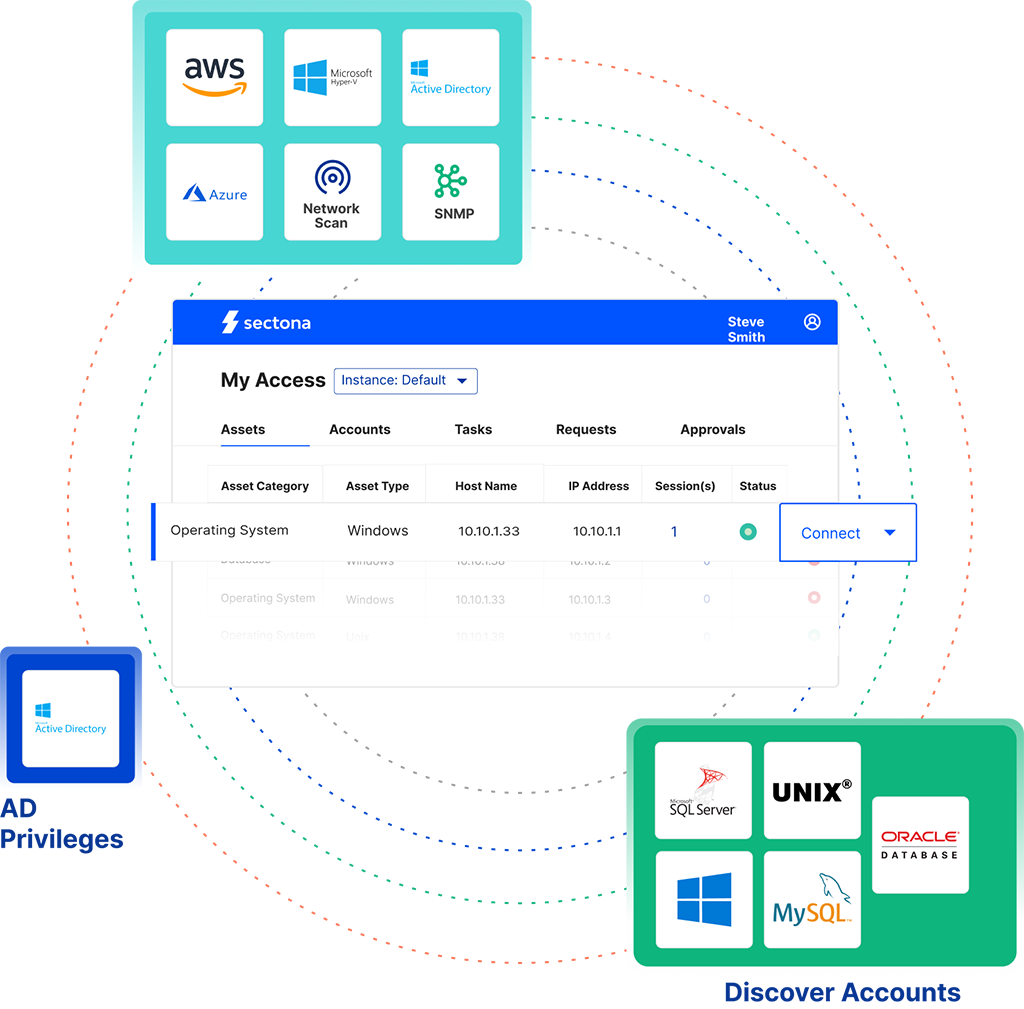
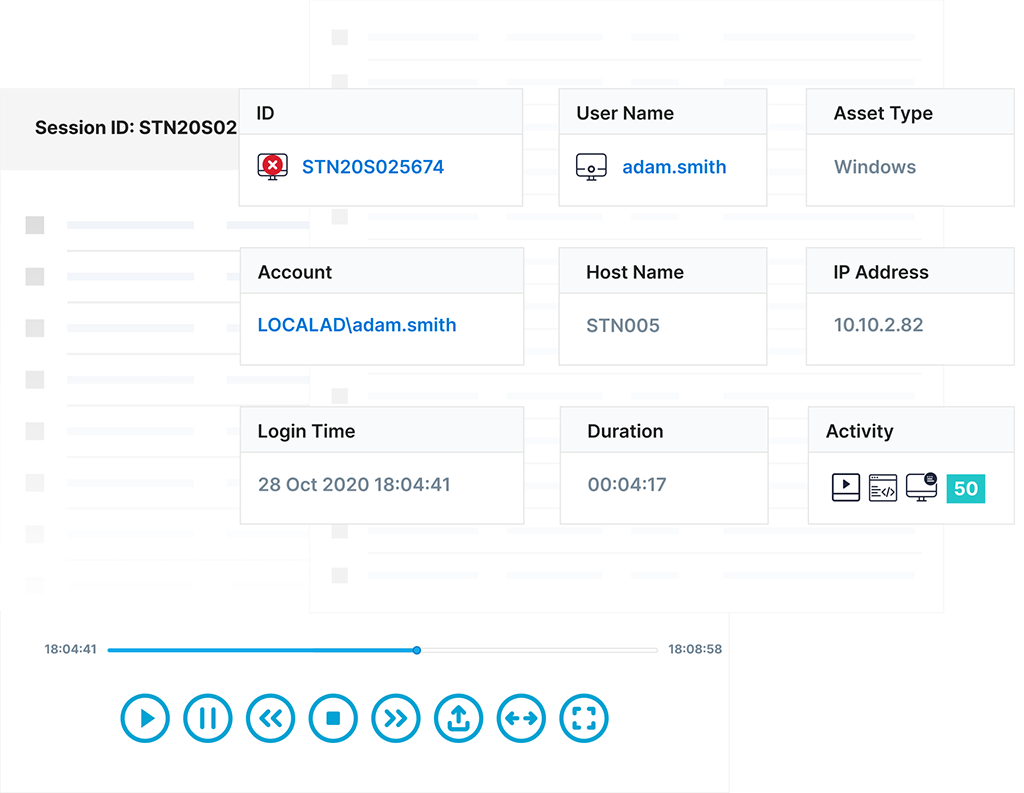
Monitor, govern & analyze privileged activity
Track and maintain comprehensive logs of each privileged session while gathering risk-based threat intel
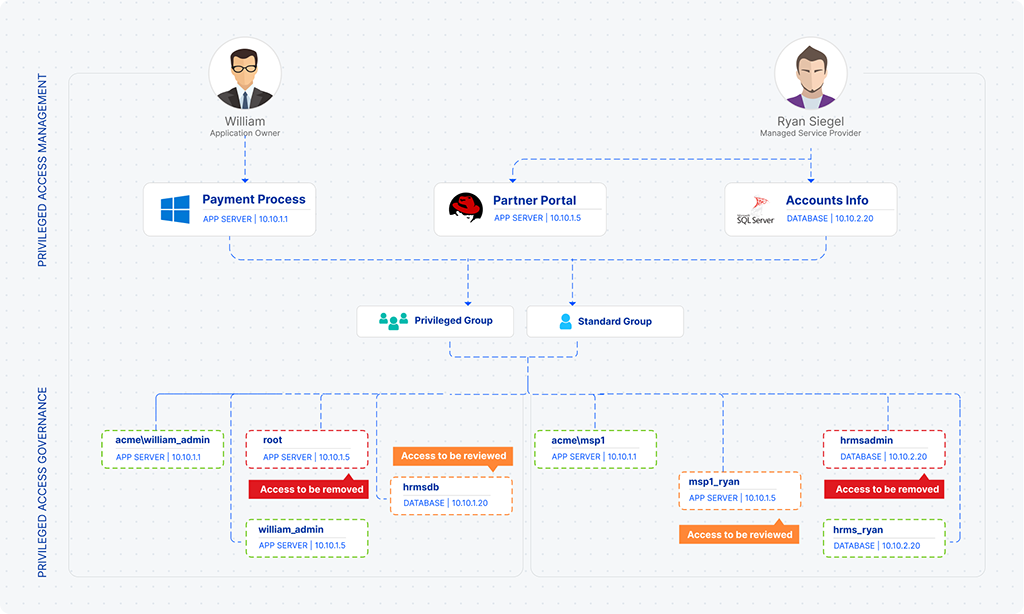
Integrated Privileged Access Governance
Automate periodical review of entitlements and certification of access to PAM platform
USE CASES
From securing what matters to advanced access challenges
Application Password Management
Secure passwords and secrets stored across config files or scripts or hardcoded in applications
Distributed Architecture & HA
Easily deploy PAM across regions or sites, on cloud or on-premises with built-in replication capabilities while maintaining flexibility to manage authentication centrally or via distributed approach
Service Account Management
Stay in control of service accounts spread across your IT with dedicated service account discovery and password management
Extensible API
Leverage RESTful APIs from the platform to stitch your apt technology stack and journey
Simple Connector Development
Integrate and manage access to custom applications and/or plugins on the fly without increasing overheads and developing specific internal skillset
Trusted by Leading Organizations
Implement in minutes and onboard workloads across multiple clouds. Empower every team, from vendors to application users, via a single platform.


Case Study | 2 min. read
93 year old Dhanlaxmi Bank upholds mission of innovation and customer satisfaction with Sectona


Case Study | 2 min. read
RSwitch uses Sectona PAM for secure transaction processing, in line with the RNDPS


Case Study | 2 min. read
Nation’s best broker secures platform that facilitate over 800,000 trades per day with Sectona


Case Study | 2 min. read
A Pioneer Packaging Group Trusts Sectona to Secure its Infrastructure to help Deliver World-class Services


Case Study | 2 min. read
Find how EGI secures business critical applications with Sectona to deliver excellence round-the-clock





Everyone Covered
No matter where you are in your journey of managing privileges, we have the resources to help you get started.
PAM 101 Resources
Further your privilege and access management knowledge and learn how to use Sectona PAM to securely access critical systems
Documentation
Further your privilege and access management knowledge and learn how to use Sectona PAM to securely access critical systems
View Sectona Docs
Training Certifications
Looking to get trained for Sectona Courses, Certifications. We offer multiple training programs to get you started.
Get started with your personalized demo
Talk to a technical expert to know more or get an overview of our technology.
Get started with your personalized demo
Talk to a technical expert to know more or get an overview of our technology.
Error: Contact form not found.