Endpoint Privilege Management
Control and secure administrator account usage on endpoints
Manage Administrator Privileges and Control Application Usage on Endpoints
Allow normal users to elevate applications with option for time-limited rights. Achieve more control on application usage through policy management.
Zero Trust Security
Integrated privileged management for diverse IT Teams
Demonstrate Compliance
Designed to help you secure endpoints, workloads and applications with a consolidated dashboard
Prevent Ransomware and Malware
Purpose built to cater to emerging security needs capable of handling scalability and complex enterprise requirements
USE CASES
From securing what matters to advanced access challenges
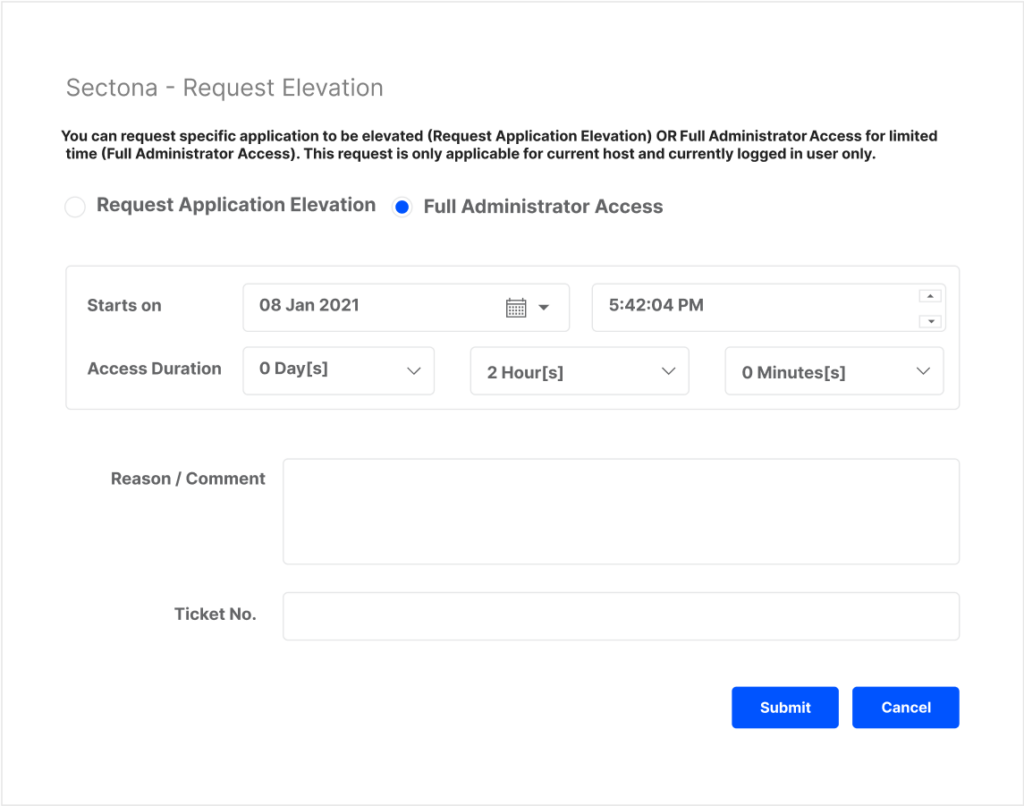
Allow users to elevate privileges on-demand
Define trust-based policy to allow users elevated privileges on-demand for accessing applications needing administrator rights.
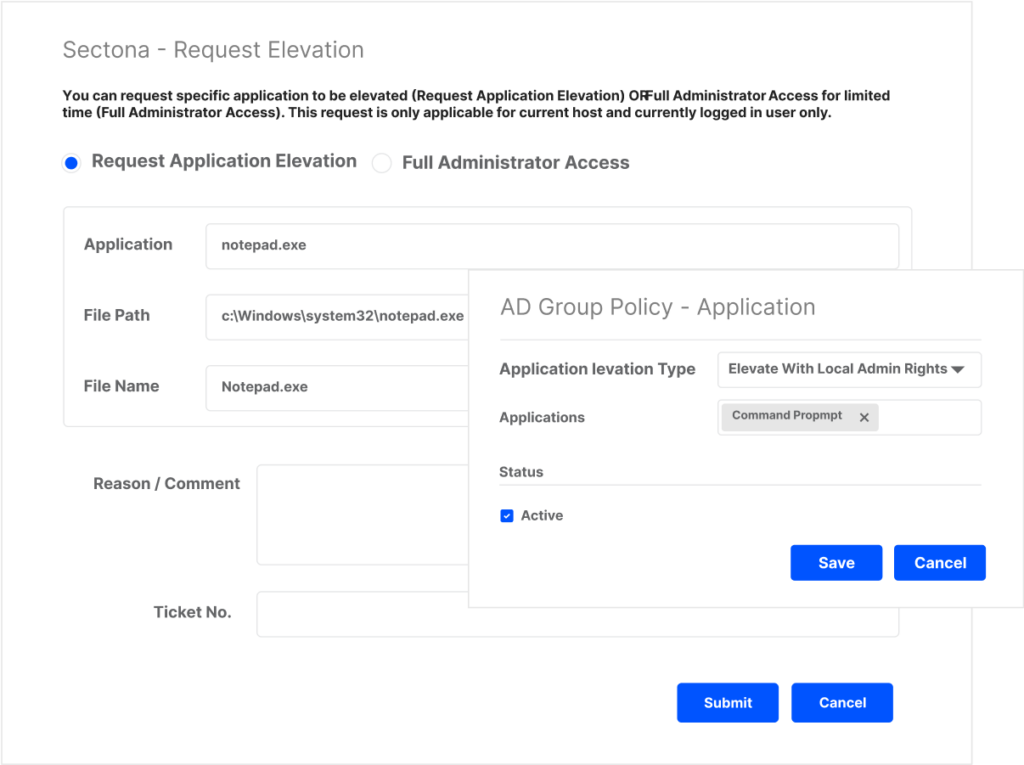
Empower users with controlled & need-based administrator access
Users can request administrator rights and access for a specific application or for a defined time to perform administrative activities.
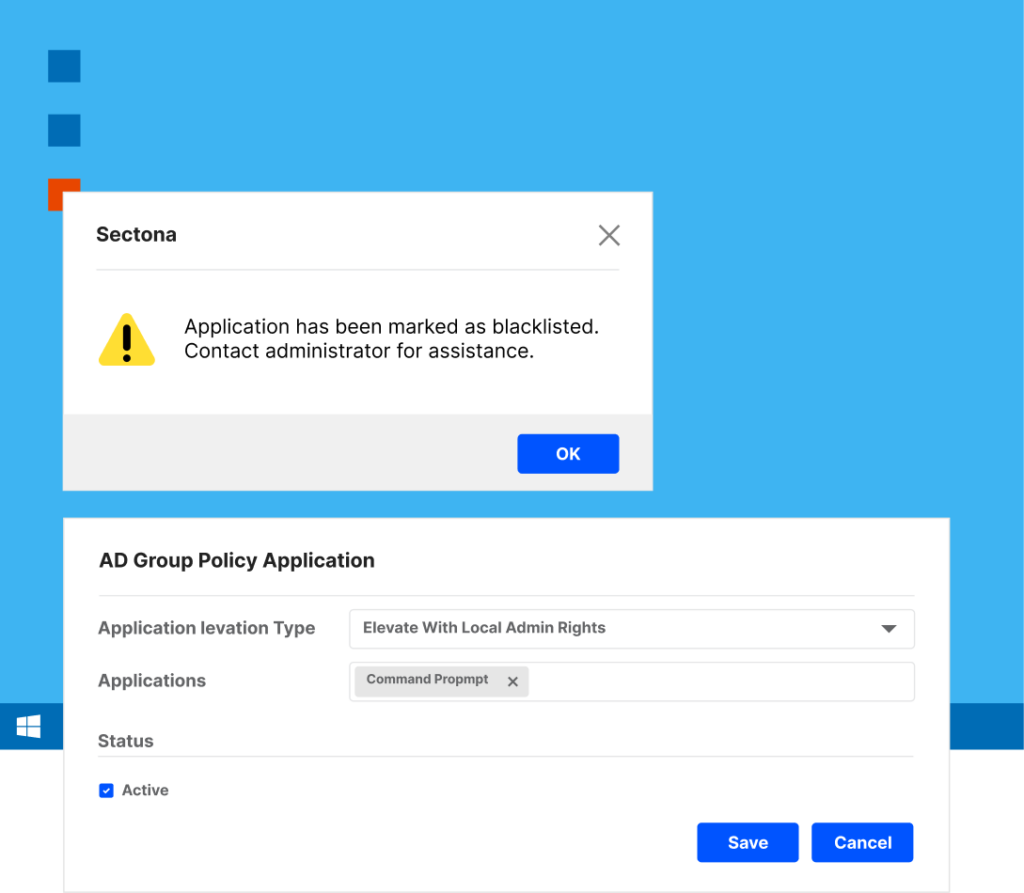
Application Control
Enable users to access trusted applications only and facilitate request-based access otherwise.
Offline Scenarios
Authorize remote workforce outside LAN or without internet to access securely.
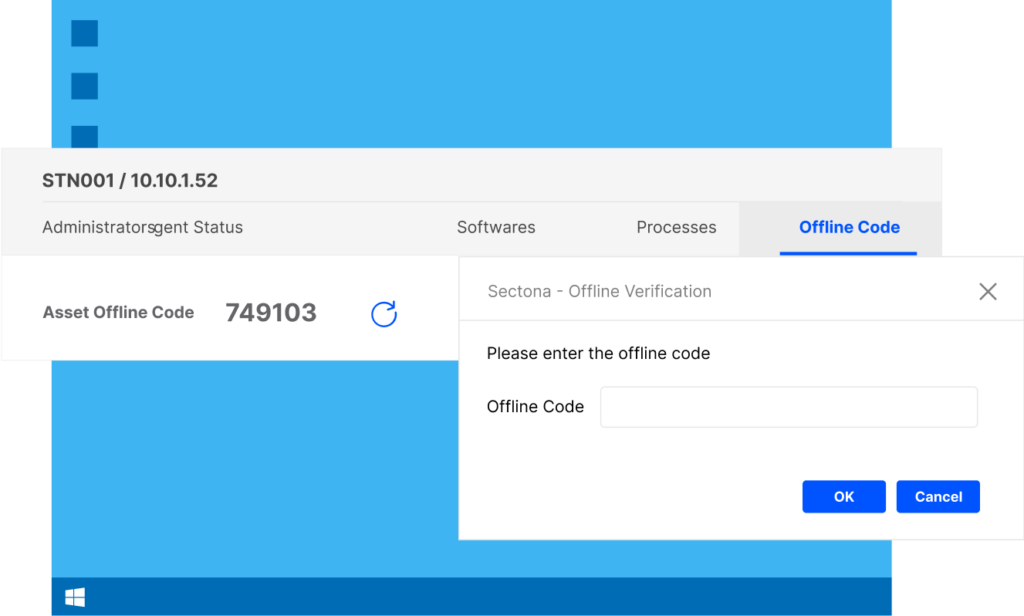
Remove & Continuously Monitor Administrator Rights
Stay in control of administrator rights granted over a period of time and keep track of usage of local administrator privileges with special reports.
FEATURES
From securing what matters to advanced access challenges
Windows And Mac Protection
Control and secure administrator account usage across Windows and Mac endpoints.
Workflow Controls
Facilitate workflow-based policies to enable secure access for users.
Centralized Policy Management
Centrally control least privilege policy. Allow apps & processes to be elevated on endpoints for specific users or groups.
Inventorize Assets
Dynamically profile and inventorize endpoints in your organization and easily implement least privilege policies
Password Management
Secure local administrative passwords with solution’s purpose-built embedded vault.
Automated Updates
Centrally push updates and agents required for managing endpoints.
Applications Discovery
Discover applications automatically that needs administrative privileges..
Extensible API
Leverage RESTful APIs from the platform to stitch your apt technology stack and journey
Trusted by Leading Organizations
Implement in minutes and onboard workloads across multiple clouds. Discovery, Secure Passwords and Secrets. Empower every team from vendors to application users via a single platform.


Case Study | 2 min. read
93 year old Dhanlaxmi Bank upholds mission of innovation and customer satisfaction with Sectona


Case Study | 2 min. read
RSwitch uses Sectona PAM for secure transaction processing, in line with the RNDPS


Case Study | 2 min. read
Nation’s best broker secures platform that facilitate over 800,000 trades per day with Sectona


Case Study | 2 min. read
A Pioneer Packaging Group Trusts Sectona to Secure its Infrastructure to help Deliver World-class Services


Case Study | 2 min. read
Find how EGI secures business critical applications with Sectona to deliver excellence round-the-clock





Everyone Covered
No matter where you are in journey of managing privileges. We have resources to help you get started.
Documentation
Further your privilege and access management knowledge and learn how to use Sectona PAM to securely access critical systems
Get started with your personalized demo
Talk to a technical expert to know more or get an overview of our technology.
Get started with your personalized demo
Talk to a technical expert to know more or get an overview of our technology.
Error: Contact form not found.