Satellite Vault: Ensuring Business Continuity Amid Disaster Outages

What is Satellite Vault?
It reduces the number of instances to ensure high availability of applications and creates offline password storage with limited and secure resources. It is a stand-alone module that securely replicates passwords and secrets from your primary vault instance to other instances. Users can enable the satellite vault if the primary vault is unavailable during unplanned downtime, system faults, data errors, or site outages.
What is a Break Glass Scenario?
A Break Glass Scenario metaphorically depicts a situation of smashing the glass of a fire alarm and immediately getting the necessary help in case of a disaster. Extending the analogy, in terms of Privileged Access Management, a Break Glass Scenario refers to an emergency where the business processes critical to the functioning of an organization are at a halt with no way for users to restore them online, leading to outages and business ramifications.
Break Glass Scenarios can be caused by a network outage, application fault or a natural disaster. These outages can disrupt the regular operability of a PAM Solution when deployed in a standalone or single-site mode; users perform a Break Glass checkout or reset of credentials when they need immediate access to restore normalcy from the outage situation.
The common Break Glass Scenarios where credentials are recovered from a secure location are:
When emergencies arise when direct access to PAM System is blocked, gaining access out of the purview of the standard operating procedures
- When mission-critical systems are down.
- And when credentials must be retrieved from a physical storage device.
- Organizations have been looking for such solutions that ensure that their privileged users have access to credentials to their resources in all risk scenarios.
How Does Sectona’s Satellite Vault Work?
When sophisticated IT systems and environments fail despite numerous levels, protections, and redundancy, Sectona uses the Vault to sync User passwords on a real-time basis, ensuring that the user has access to the system 24×7. Therefore, in case of vault failure, the user can acquire a password with the help of the Vault and can access the system.
Where Should You Install a Satellite Vault?
As a best practice, the Vault should be set up on a secure machine (workstation/laptop) on the same network as Password Vault. In addition to this, service related to this vault should be ON and running in PAM – this ensures real-time sync of the passwords.
When the Satellite Vault service is active, the Password Vault sends a copy to ‘Satellite Vault’ whenever it is changed according to the password rotation policy to keep the most up-to-date copy of the privileged account passwords.
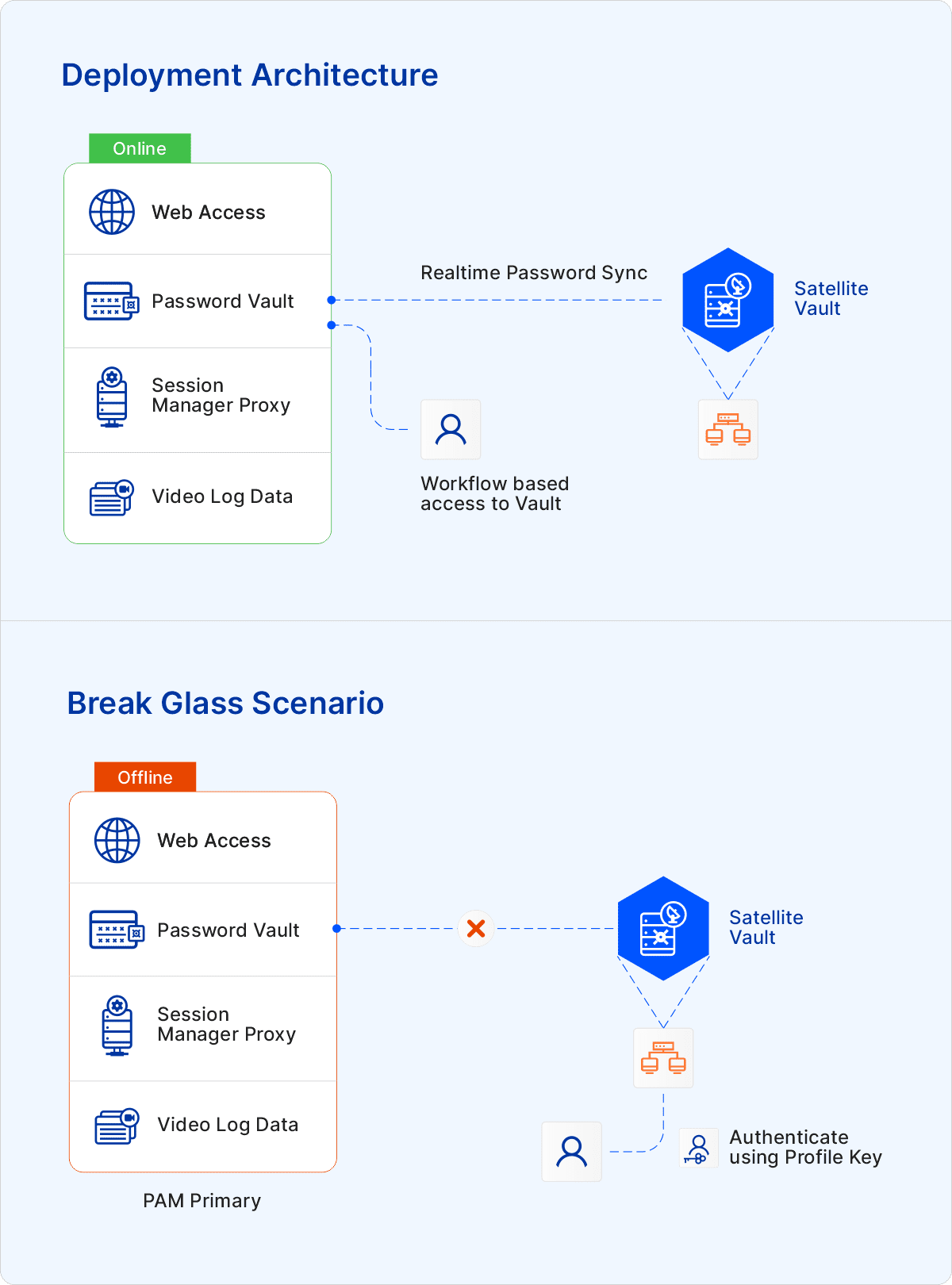
Now, let’s take the scenario of unplanned downtime. Let us suppose that due to an unexpected shutdown, the users are unable to access the system. In this case, the user will need to use the security key provided by the administrator to access the credentials. The security key verifies the user’s legitimacy and authenticity at the satellite vault level. It includes authentication at vaults without requiring a separate database or authorization source, such as Active Directory, typically unavailable in disaster situations.
Users with administrative rights can copy their Profile key into the Satellite Vault system using Windows login credentials. Admin user has privileges to generate the security key by logging into their primary vault profile.
User authentication is based on a security key for accessing passwords/secrets at the vault level. The vault uses key-based authentication rather than an authentication database to recognize a user.
A Security Key generated from the User Profile will be required to log in to Satellite Vault. To log in correctly, the administrator must sync the users’ profiles with their accounts. Only after the sync is complete should users download the Security Key. The user must upload the key to the vault to log in.
Customer Success Story
- A manufacturing company stored SAP Application login access to their root accounts on an envelope using a specialized printer. The company sealed the credentials in a locker and made it accessible only to a few employees.
The company wanted to digitize this process and introduced Sectona’s Satellite Vault (as a digital vault) and stored credentials in the PAM vault.
With this step, the credentials got replicated to the satellite vault with the same level of encryption. It also ensured that access to employees in the organization during a Break Glass Scenario was restricted and reduced the time-consuming process of manually storing login credentials on an envelope.
- A payment gateway company was planning to store their passwords in a digital vault so they could access these credentials remotely during a Break Glass Scenario. With the implementation of Sectona Satellite Vault, they secured their passwords in a digital vault, restricted access and adhered to the compliance regulations.
Conclusion
It is essential to define how and where you place Satellite Vault, and this must be one of the crucial design decisions in planning your business continuity.
Related Reading: How to Securely Store and Retrieve Privileged Credentials?



