Password Management in Network Security: What is it? Why is it Crucial?

Passwords are the first line of defence for every digital asset. As the threat of credential theft is increasing, it is essential to have a robust enterprise password management policy to secure business-sensitive assets and critical infrastructure.
In this post, we discuss the importance and working of password management in network security.
Password Management
Passwords, records, and digital identities are sensitive data that can be stored and managed by enterprise password management systems. When an employee leaves or a department reorganizes, a password manager makes it easy to reset their login credentials.
In large organizations, entering and managing passwords is tedious and challenging. However, any company’s IT and security departments must pay close attention to the administration of approved accounts held by humans and non-humans. To lessen the likelihood of password-based attacks, it is recommended that businesses check their password management processes regularly. In addition, passwords should be reset, cycled, or revoked whenever an employee is promoted or receives a new position.
With the expansion of the digital landscape, the number of users and their passwords is also increasing. This proliferation made it challenging for businesses to manage passwords manually – demanding the need for automated enterprise password managers.
The Working of Password Management in Network Security
An encrypted storage facility (password vault) for sensitive information is at the heart of any enterprise-grade password manager. Instead of keeping track of several passwords on post-it notes or in unreliable spreadsheets, employees may retain their credentials, including SSH (Secure Socket Shell) keys, in a single, readily accessible location inside the vault.
The vault uses a master key to encrypt the database of passwords and secrets; you need only remember this one password, which you enter when you first log in to your vault at the beginning of each session.
Upon logging in, the password manager uses your provided information to populate login fields on other websites. Any time you fill out a form that requires an account, and you still need to do so, the password manager will establish a secure password for you and store it in a secure vault. You only must log in to your vault once and have instant, automated access to your company’s online accounts.
As an IT administrator, you may perform two things with the help of the advanced administration and reporting features included in enterprise password management systems.
To begin, you may set up rules for how users should create and share passwords. Second, enhance the platform by generating data showing how users engage with it and how secure your company’s passwords are on a per-user basis.
The Three Crucial Basics of Password Management in Network Security
- Complexity
Passwords should be complex to guess. Short passwords may be readily broken using brute force techniques like a password cracker. Therefore, your password should be at least eight characters long. It is recommended that employees use passwords that include a number and a unique character (such as:!, £, $, or %). Standard terms in a password, such as “password” or “let me in” or the employee’s city or nationality, should be avoided.
Ask your staff not to use easy-to-guess passwords. For example, their name, or the names of their family members, should not be used as a password.
- Frequency
Passwords should be changed frequently to limit the risk of leaks. The standard period is 90 days. Although it might be annoying for workers who must constantly remember new access credentials, password rotation is an effective way to limit the probability that workers would use the same password for their work and personal accounts. As a further security measure, it is recommended that system administrators implement a “no-reuse-of-previous-passwords” policy.
- Centralization
Password managers are no different from any other cybersecurity solution needing an easily accessible centralized administration dashboard. Password restrictions, such as mandatory master passwords, authorization to share passwords, and maximum failed login attempts before blocking an account, should be configurable from the admin dashboard.
The Benefits of Automating Enterprise Password Management
- No More Password Load
Employees can use the same password for numerous corporate applications without remembering them. Potential collaborators and contractors may need temporary login credentials. They may be created, monitored, and deleted after their work is done with the company. Third-party network access can also be monitored and recorded throughout your sessions, and you can grant them access if necessary.
As BYOD (Bring Your Device) becomes more widespread, cloud-based password managers provide the added benefit of making passwords accessible from any device.
- Maintain Compliance and Fix Rapidly
Any password policy is useless if users choose to disobey them. An enterprise password management solution allows IT to monitor employee password habits, allowing for the early detection and correction of non-compliance issues. Even a single password leak may have catastrophic consequences. However, with proper controls in place for auditing and reporting, the threats can be avoided.
- Achieve Operational Efficiency
Having your IT help desk spend time responding to employee password reset requests is time-consuming. However, once their password reset request is dealt with, workers will likely be able to do their jobs. By removing these obstacles, a password manager helps workers become more efficient.
- Protection from Credential Theft
Password reuse is expected because no one can remember many different passwords. However, in the commercial world, it might have disastrous consequences. This implies that an attacker who gains access to one service may get access to others and steal data from them with only one compromised password.
Using a password manager makes using unique passwords for each service simple, reducing the potential fallout from a breach in any area. Further, password management tools may keep tabs on password use, notifying management and the employee when password hygiene is breached.
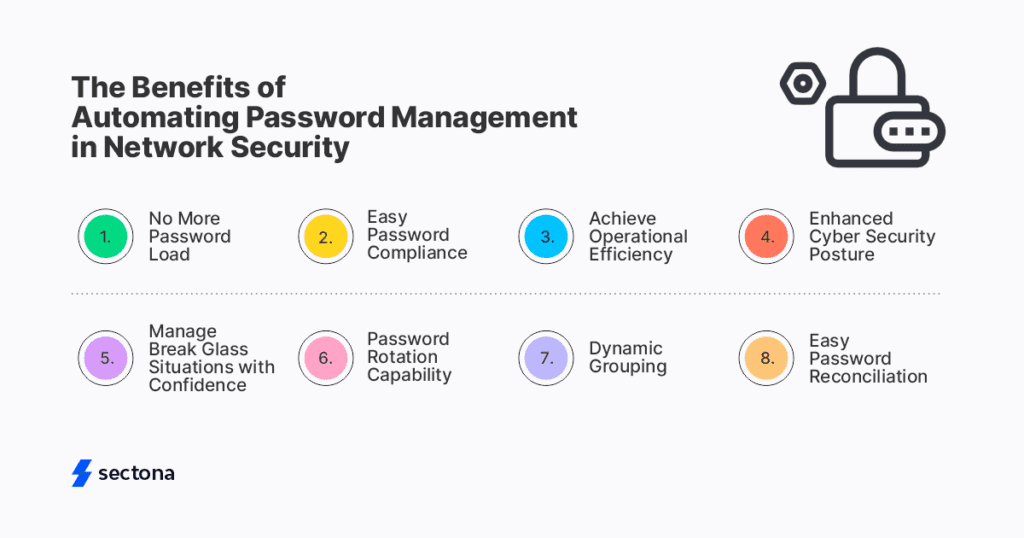
Added Advantages with Sectona Security Platform
Sectona PAM (Privileged Access Management) comes with an inbuilt password manager to strengthen your network security posture. The tool simplifies protecting privileged credentials and SSH keys with embedded vaulting capability. Here are more ways how you can leverage Sectona’s Password Manager.
- Manage Break Glass Situations with Confidence
Disaster planning and recovery are critical aspects of an IT security strategy. During service disruptions such as cyber-attacks, web server failures or prolonged power outages, your IT teams can securely sync passwords to Sectona’s standalone vaults and retrieve them. These are called satellite vaults, following the same security and encryption techniques as the primary vaults.
- Password Rotation
Get the most by limiting the lifespan of passwords and mitigating the risk of a security breach with password rotation. Reduce manual efforts of resetting privileged user passwords and storing them. The password manager helps you reset users’ credentials to new values on a pre-defined schedule and store them centrally in an encrypted vault.
- Dynamic Grouping
Dynamic grouping helps you discover asset types based on attribute values such as asset types and naming conventions. After finding your privileged assets, the tool enables you to simplify access and password management policy assignment, thereby reducing the time to onboard new accounts.
- Easy Password Reconciliation
Achieve consistency and security between passwords stored in a central vault and those on an organization’s IT resources with Password Reconciliation. With this methodology, your privileged users can easily access the resources needed without interruption and exposure to any potential breach. With password reconciliation, you can ensure the ultimate protection for your IT resources, not compromising the ease of access.
Planning to implement password management in your enterprise? Our white paper, Simpler, Faster and Complete Password Management, can help you.
Do you want to know further details about the importance of password management in network security? Read our solution brief for more information.



