Threat Analytics
Intelligence System for monitoring and assessing
What is Threat Analytics?
Threat Analytics is a system that enables an organization to monitor activities of all user sessions, analyze the impounding risks/threats, and take precautionary measures to reduce the impact of an attack going forward. It helps you understand potential risk points or attack surfaces around user activities with the help of Machine Learning algorithms that derive counterintuitive measures to avoid such illegitimate activity.Threat Analytics in a PAM Solution: –
With the world looking towards a digitalization era, the stability of business in each and every sector is affected by cyberattacks that are leaving organizations in a vulnerable and impermeable situation.
Hackers are becoming more sophisticated by the day, leading to huge information losses or economic losses. They can be targeting the organization externally or as an insider irrespective of which it is imperative that we work on mitigating the impounding risk.
Threat Analytics is a system that enables an administrator and an auditor to keep track of all activities in each user session, analyzing and working on measures necessary to keep the organization’s environment safe and secure from any attack.
What are the Challenges Faced in Threat Analytics?
One of the biggest challenges that often affects threat analytics is disturbances created by false positives generated by security tools and their algorithms.
Why Threat Analytics Need to be Re-Engineered?
Threat Analytics needs to be reengineered to identify and discard false positives in order to provide a robust analysis when dealing with large amounts of data.
What is Privileged Threat Analytics?
Privileged Threat Analytics is a more streamlined approach that protects the organization’s environment from cyber-attacks and insider threats pertaining to privileged account use. It takes information from multiple data points and studies the behavior of all critical entities in the organization.
Privileged Threat Analytics analyzes the information and aligns itself to detect any kind of malicious activities, abnormal behavior and analyze any vulnerabilities posed by the existing protocols in the system around focused areas of privilege misuse, privilege abuse, and data theft.
This analysis is put in motion via Machine Learning and Behavior Analytics processes. It also enables the auditor to track all events and if a malicious activity of critical risk is found, it helps to trace back to the roots of the event to reduce the risk.
Sectona’s Advanced Threat Analytics (ATA): –
Sectona’s Privileged Access Management solution helps avoid threats and discrepancies from any kind of attack vector.- Sectona’s Advanced Threat Analytics provides a Risk Scoring feature, which analyzes the activities for each session based on 30+ varied yet focused parameters that are common modes of privileged account attacks. The risk scoring level is set with 4 different values ranging from low to critical and whose configuration values can be adjusted according to the requirement. This score gives us an insight into the criticality of risks during each session enabling us to prioritize and identify any anomalous activities persistent or posing as a threat and act on them to mitigate the risk.
- Sectona ATA also provides an advanced feature, that of Privileged Account Analytics which connects to all Windows and Unix Operating-System-based resources and collects information pertaining to the logs in real-time. These logs are in turn compared with the PAM user and server logins and designed to notify if it triggers attacks like Brute Force Login attempt, Pass the Hash Attack, or Compromised server. Privileged Account Analytics has been designed to reduce the workload on PAM solutions, offering a centralized view of the logs pertaining to operating-system events.
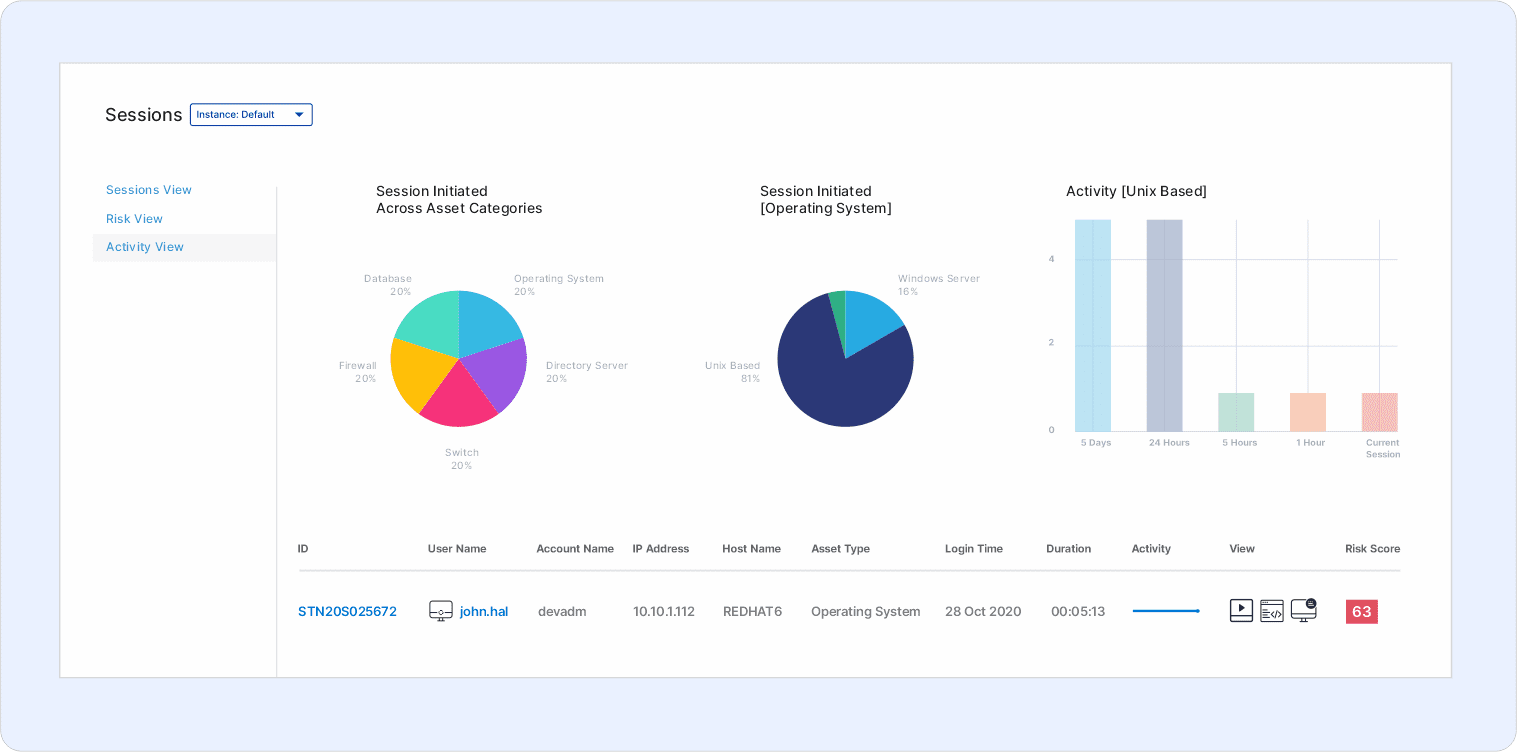
The preview below gives an overview of the activity, the events, and video logs accommodating with the risk score to assess the sessions’ behavior and threat level.