Interactive Accounts
Safeguard and Secure accounts accessing and running programs on Target Assets
What are Interactive Accounts?
Privileged Accounts are of two types – Interactive Accounts and Non-Interactive Accounts. Interactive-Accounts, as the name suggests, are accounts that can help users gain access to the systems and run programs with the help of a password. Non-Interactive Accounts, on the other hand, are non-human accounts that interact with the operating system directly and run services automatically without any human intervention, as they do not require any login credentials.
How can Sectona PAM Safeguard such Accounts?
Sectona’s Privileged Access Management solution facilitates safeguarding and secure access to both Interactive and Non-Interactive Accounts. The solution ensures that the credentials of interactive-accounts and those in clear-text or hardcoded form elsewhere leveraged by non-interactive accounts are securely vaulted and used at the time of need. Without exposing the credentials of such accounts to users, the solution ensures seamless operations and transparent, secure access for the usage of both interactive and non-interactive accounts. Below is an overview of the authentication process of interactive and non-interactive accounts, followed by different accounts falling under each classification.
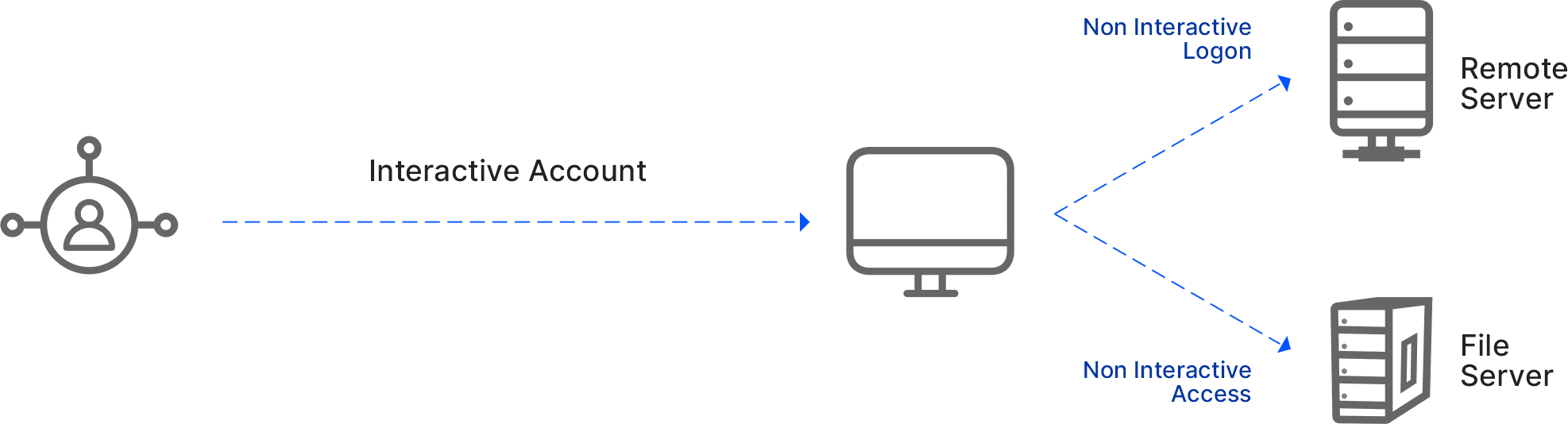
1) Interactive-Account Authentication: Interactive logon authentication process grants users, access when they enter credentials using a local or domain user account for a corresponding logon, respectively. The interactive authentication process validates the user’s identity with a security account database on a local computer or directory service on a domain.

2) Non-Interactive Account Authentication: Non-interactive authentication happens after an interactive authentication has taken place, during which the user does not input login data but instead uses previously established credentials. A non-interactive user is not a typical user; it is more an access mode that is created with a user account, which is a mechanism where a user does not have to re-enter login credentials when they want to access multiple systems. For example, In Windows, a non-interactive authentication takes place when establishing a secure network connection by an application using the Security Support Provider Interface (SSPI) and security package.
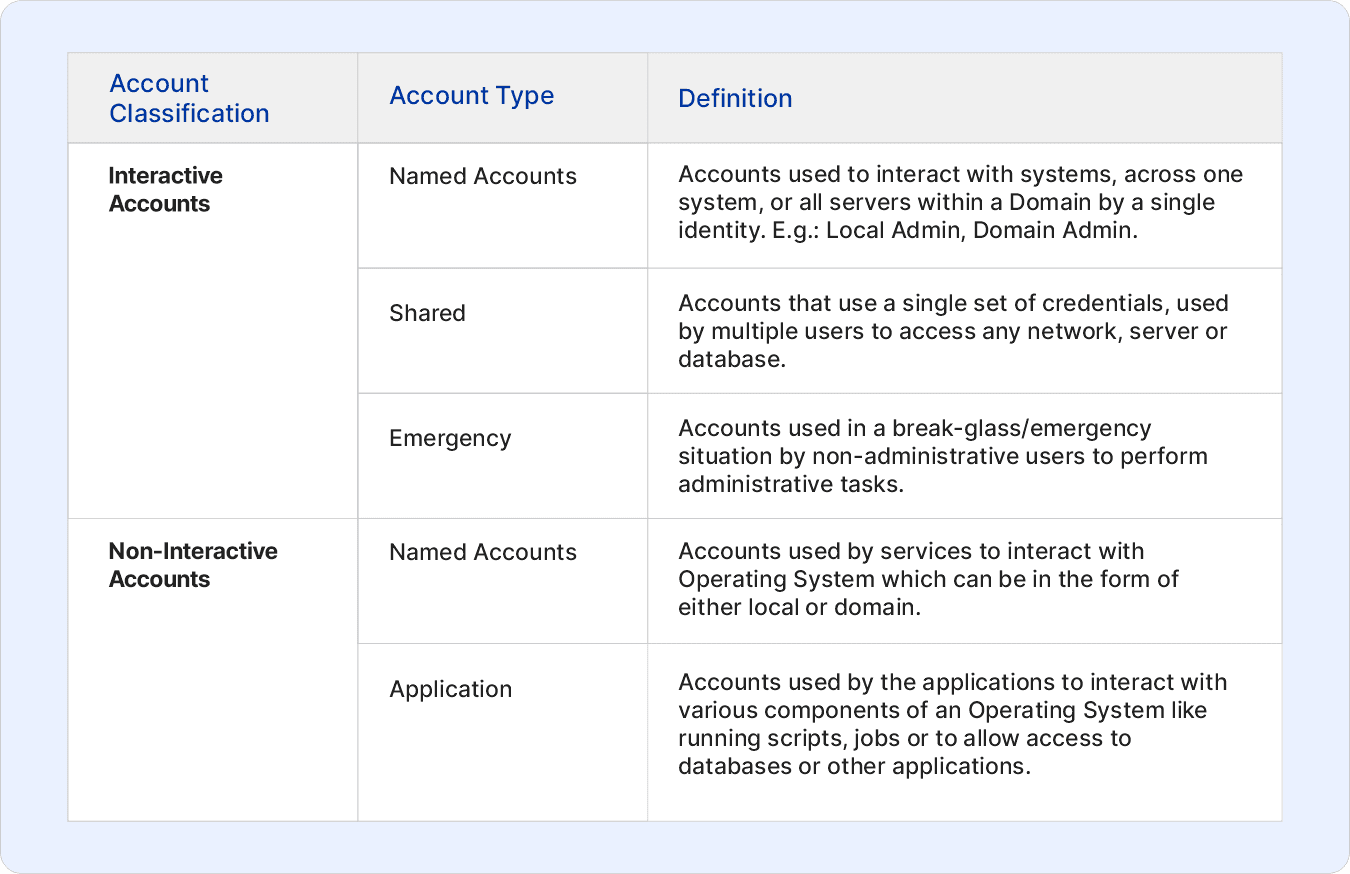
 3) Account Classification
3) Account Classification