What is Role-Based Access Control?
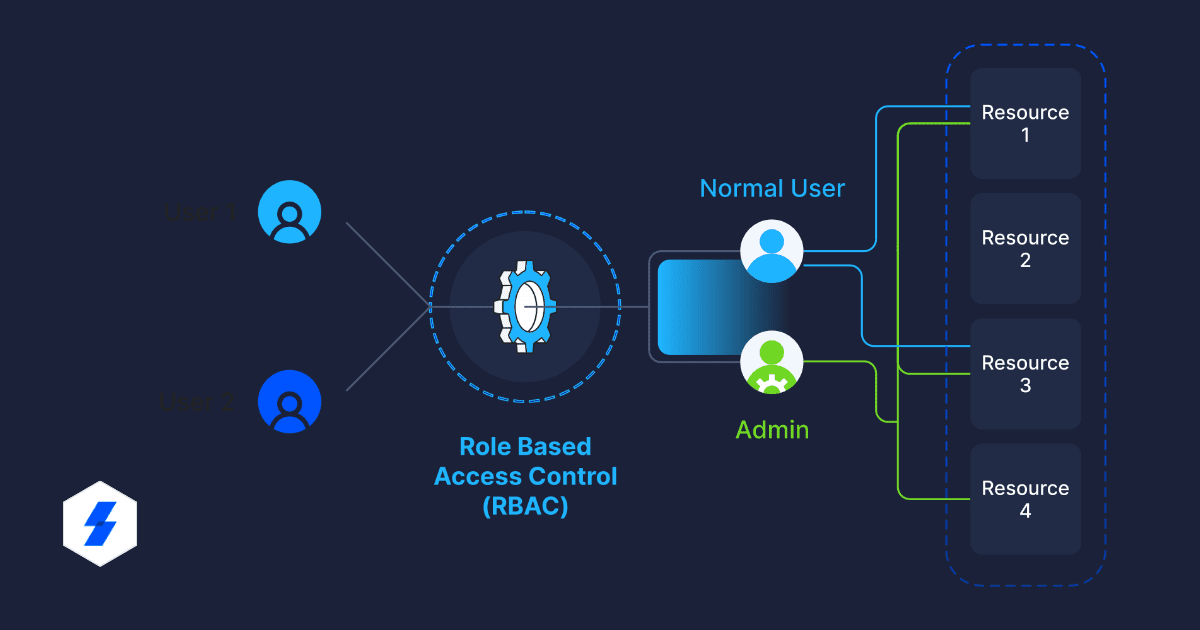
Role-Based Access Control (RBAC) is a cybersecurity concept for creating permissions for employees based on their role within an organization. The RBAC rules can be applicable to an individual user, a group, or multiple groups.
With RBAC in place, organizations can allow employees to access only the necessary resources to perform their duties. Authorities, responsibilities, and skill levels are a few criteria to assign roles in this model.
RBAC is an essential security measure for preventing the misuse of user access to critical systems and data. More importantly, the model is vital for managing access in dynamic organizations with numerous employees, remote users, and third-party vendors.
With RBAC in place, organizations can allow employees to access only the necessary resources to perform their duties. Authorities, responsibilities, and skill levels are a few criteria to assign roles in this model.
RBAC is an essential security measure for preventing the misuse of user access to critical systems and data. More importantly, the model is vital for managing access in dynamic organizations with numerous employees, remote users, and third-party vendors.
Examples of Role-Based Access Control
Using Role-Based Access Control, businesses may label employees as administrators, power users, or regular users based on their role’s need to access resources. Some further possibilities are:
- In IT companies, developers have access to various resources and tools like GitHub, Visual Studio and AWS to build software applications but have no access to employee directories. An HR manager has access to HRMS with employee records, while marketers possess access to Content Management Systems (CMS) and social profiles.
- In a healthcare system, there are distinct roles, such as doctors, nurses, and administrative staff. With RBAC, doctors have access to patient medical records, while nurses have access to patient vitals, medication records, and so on. Administrative staff have limited access to patient records and may only view non-sensitive information such as appointment schedules.
- Employees in a financial services company have different access levels to customer data, transactions, and financial reports. For example, tellers have access to customer transaction records, account managers possess access to customer account details and financial analysts access financial reports and analyses.
Multiple access management and contribution layers may exist within each assigned role, with its own set of privileges and responsibilities.
When people join a group with specific responsibilities, they get access to all the resources pertaining to those roles. To limit a user’s privileges, you may remove them from a group. Adding users to numerous groups is another method to provide them with temporary data or application access.
When people join a group with specific responsibilities, they get access to all the resources pertaining to those roles. To limit a user’s privileges, you may remove them from a group. Adding users to numerous groups is another method to provide them with temporary data or application access.
What are the Benefits of Role-Based Access Control?
- What are the Benefits of Role-Based Access Control?
Using RBAC, access is granted only at the level necessary to complete a task. As a result, the likelihood of data breaches and leaks can be reduced. With RBAC in place, the damage is limited if a breach occurs since the attacker’s intrusion point is restricted to certain endpoints that can be zeroed in quicker.
An additional layer of security is added by the RBAC concept, Separation of Responsibilities (SoD). Separating responsibilities ensures that each role is accountable for specific tasks and no person has complete control over any given function. For example, Insiders who misuse their access privileges can be a significant security threat to organizations. Separating duties and permissions can mitigate this risk by making it more difficult for a single user to cause damage or steal data.
An additional layer of security is added by the RBAC concept, Separation of Responsibilities (SoD). Separating responsibilities ensures that each role is accountable for specific tasks and no person has complete control over any given function. For example, Insiders who misuse their access privileges can be a significant security threat to organizations. Separating duties and permissions can mitigate this risk by making it more difficult for a single user to cause damage or steal data.
- Streamlines Processes
By only providing users with the permissions, they need to do their jobs, RBAC makes it easier to get rid of bottlenecks. Users will no longer need to hassle administrators to use internal resources. Additionally, IT teams can be released from the tedious task of managing numerous individual user accesses.
To a substantial extent, RBAC streamlines the user account delegation including provisioning/ de-provisioning and management. Administrators can make the necessary changes quickly and efficiently, whether for a current employee who is promoted inside the company or a contractor or external user who needs temporary access to your network.
To a substantial extent, RBAC streamlines the user account delegation including provisioning/ de-provisioning and management. Administrators can make the necessary changes quickly and efficiently, whether for a current employee who is promoted inside the company or a contractor or external user who needs temporary access to your network.
- Improves Compliance
Implementing RBAC can improve compliance with regulatory frameworks such as HIPAA, GDPR and PCI DSS. RBAC provides broad and granular levels of access controls for securing user accounts and ensures that access privileges are always up to date – an essential part of complying with security guidelines.
In addition, RBAC provides a clear audit trail of who accessed what data and when. This can help businesses comply with regulations that require organizations to track and report on access to sensitive data.
In addition, RBAC provides a clear audit trail of who accessed what data and when. This can help businesses comply with regulations that require organizations to track and report on access to sensitive data.
How to Implement Role-Based Access Control?
Find Out What Your Company Requires
Before implementing RBAC, you must start by thoroughly evaluating your company’s operational requirements. The analysis aims to ascertain which job roles contribute to maintaining well-established corporate procedures and technology. In addition to auditing and other legal obligations, the RBAC policy should consider best practices.
Application Scope Identification
Before implementing RBAC, you must start by thoroughly evaluating your company’s operational requirements. The analysis aims to ascertain which job roles contribute to maintaining well-established corporate procedures and technology. In addition to auditing and other legal obligations, the RBAC policy should consider best practices.
Determining Job Roles
The findings from the requirements analysis should inform how the company defines roles, with an eye on the ease with which users can do their jobs. When designing roles, it is crucial to avoid common traps like too much flexibility, too many exceptions, and overlap.
Allocating Roles to People
The next step in implementing RBAC to manage access rights and permissions is assigning roles to employees after compiling a list of systems and describing how the workforce uses them.
Audit
Review roles, personnel, and levels of access periodically. For instance, if you find that one position has excessive privileges, you may modify the role and the privileges of all users assigned to it.
What are the Best Practices for Implementing Role-Based Access Control?
- Understand the roles and responsibilities of different employees within the organization before starting to implement RBAC. This step helps ensure that roles and permissions are correctly assigned without any discrepancy.
- Having a comprehensive policy that outlines the Role-Based Access Control model, defines job roles, and details the permissions associated with each function can be helpful in assessing and auditing your access security posture.
- Develop a comprehensive policy that outlines the RBAC model, defines roles, and details the permissions associated with each function.
- Regular access reviews should confirm that users only have access to resources they require to perform their job responsibilities. This will help identify and remove any unnecessary access permissions.
- Implementing RBAC in stages can minimize disruption and provides for an appropriate configuration of the security model. Start with a pilot group of users and gradually expand the implementation to other areas of the organization.
- Access logs and audit trails should be monitored regularly to identify potential security incidents before they cause significant harm.
- Provide employee training so they understand the RBAC model and their responsibilities within it. Employee awareness sessions help ascertain that users do not inadvertently violate access control policies.
- The Role-Based Access Control model should be reviewed and updated to ensure that it remains effective and relevant. This should include adding new job roles, updating permissions, and removing access for users who no longer require it.
Implementing Role-Based Access Control with Sectona
Sectona helps you gain comprehensive control over privileged user accounts. With our Privileged Access Management (PAM) solution, enterprises can create fine-grained access controls, customizable access request workflows and can gain clear visibility over user activity.
Learn more about Sectona or get in touch with us.
Learn more about Sectona or get in touch with us.
Related Concepts
Was this article helpful?
YesNo