Just-In-Time Access
Minimize the risks of standing privileges by granting on-demand based access.
What is Just-In-Time Access?
Just-in-Time Access is a cyber security practice of providing elevated application access to users for a fixed period of time to perform necessary tasks. JIT can minimize the vulnerabilities by reducing the risk of standing privileges, where user access to privileged applications is “always-on.”
In recent years, threat actors have grown to launch sophisticated ransomware attacks on companies, causing massive disruptions. It is also seen that privileged accounts remain the primary target for attackers as these accounts give unrestricted access to organizational critical resources and systems.
So, it is of the highest priority for us to secure privileged access from the increasing cyber menace. Traditional standing privileges can lead to privilege escalation attempts, which gives the right opportunity to hackers to move laterally across networks and further extend their malicious actions. Hence, we need strict policies and procedures, where JIT comes in handy for any organization.
Just-In-Time Access is a strategic approach based on the core principles, POLP (Principle of Least Privilege) and Zero trust policy. Just-In-Time Access ensures the implementation of these policies for any privileged access requirement, meaning nothing is trusted, and everything is verified and validated before granting elevated access. This ensures that all human and non-human users get the least privileges by default.
With Just-in-Time in place, organizations can ensure that privileged accounts are managed in accordance with the guidelines of Identity and Access Management (IAM) and Privileged Access Management (PAM).
What are the Types of Just-in-Time Access?
• Broker and Remove Access Approach
This is also known as the justification-based approach. This approach creates policies that require users to give an appropriate explanation for their need to access privileged accounts from specific locations at certain periods. Users get access when the security personnel or IT admins approve the request after validating the justification. The credentials of the privileged accounts are maintained, secured, and rotated in centrally protected vaults.
• Ephemeral Accounts
As the name suggests, this type of Just-In-Time Access works by creating new, on-demand accounts, which get revoked or deleted after use. When a user or a system requires justified privileged access for work-related activities, a new account called fly account is assigned to the user or the system with an expiry time for the account.
• Temporary Elevation
This approach of JIT works by enabling the users’ credentials to access privileged commands and actions. Once the justification is validated, a user gets elevated access for a defined time. After the completion of a limited amount of time, the privileged access expires, and the user can no longer access the elevated account.
How Does Just-in-Time-Access Work?
# Location
# Time
# Actions
Location limit ensures that the user only exercises privileged access from a pre-approved place, based on the requirement. Limiting time is the core strategy of JIT, where the user or the system gets elevated access only for the necessary time during which the work must get completed. Prevailing access gets revoked after reaching the prescribed time.
To further bring down the attack surface, JIT also limits the actions performed by the user by restricting the final parameter. With this, users can only perform requirements-based actions.
How Can Just-in-Time Access Benefit your Business?
2. JIT supports dynamic privilege elevation for a limited time, location, and actions. This practice enhances an organization’s security posture by following the best procedure in managing privilege access.
3. It also ensures meeting the compliance requirements by enforcing the principle of least privilege and removing unnecessary standing privileges. This provides a perfect, detailed, granular audit perspective for the company.
4. Privileged Access Management (PAM) becomes effortless with JIT processes. IT teams can access desired resources easily and quickly, reducing many efforts in frequent password modifications.
5. JIT also promotes effective collaboration by ensuring the user access to the actions and commands needed during the privileged windows across all the apps. When the approved time elapses, the access gets revoked.
6. In today’s world of increasing remote and hybrid work models, JIT helps with the capability to grant secured, justified, and time-bound privileges at any location across the world, thereby improving productivity.
A Few Best Practices while Implementing Just-in-Time Access
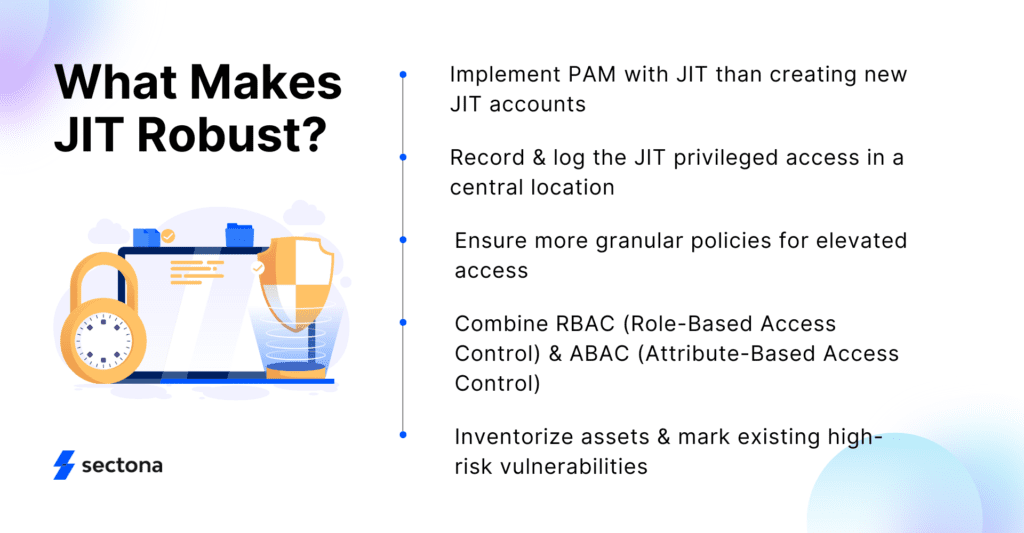
# Recording and logging the JIT privileged access in a central location ensures accurate reporting and audit.
# Policies should be more granular to demand better user justification while requesting elevated access. This validates the effective cybersecurity delivery across the organization while ensuring better PAM.
# We can include RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control) policies with JIT access. Combining these will ensure that the company addresses all practical challenges of managing privileged accesses, giving admins better control over users’ system access.
# List all the assets in an inventory and mark existing high-risk vulnerabilities in the system. This procedure ensures a better understanding of the entire security framework and helps implement PAM and JIT solutions better.
Just-in-Time Access with Sectona PAM
Get unstoppable with Sectona PAM Just-in-Time integration. Leverage automation to define custom access methods based on user access type, use ephemeral token-based integration, limit vendor access and do more. Feel free to get in touch with us and start discovering privileged accounts today. Learn more here.